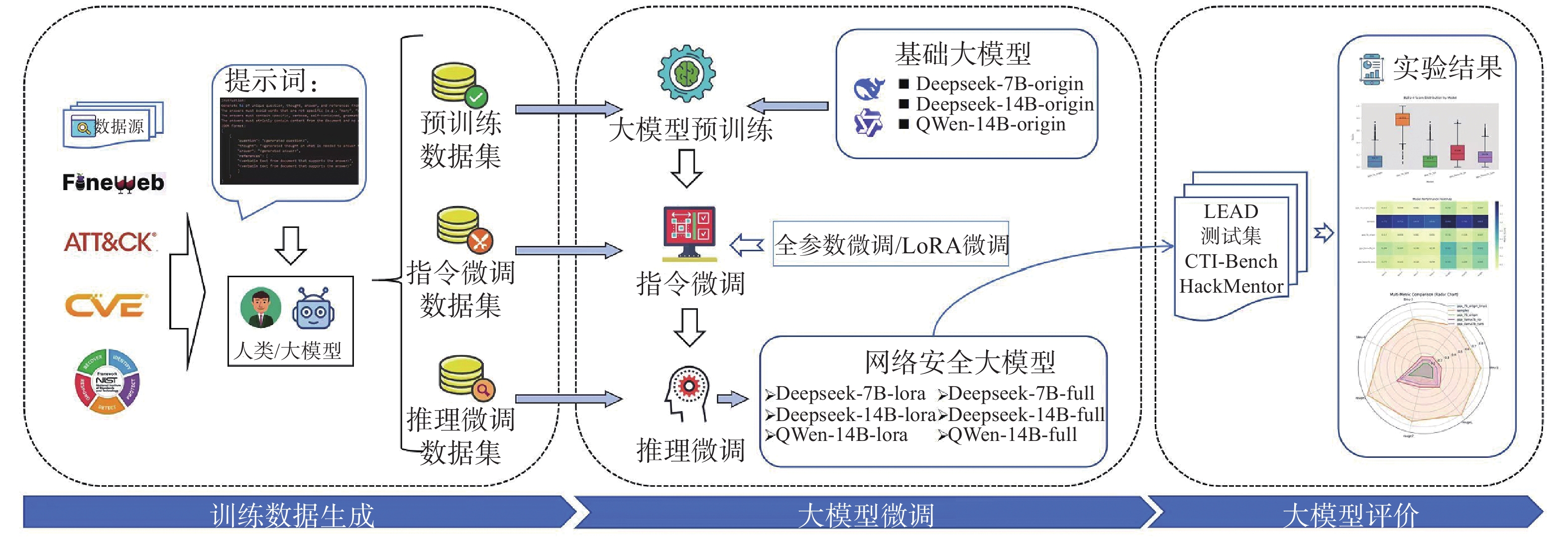
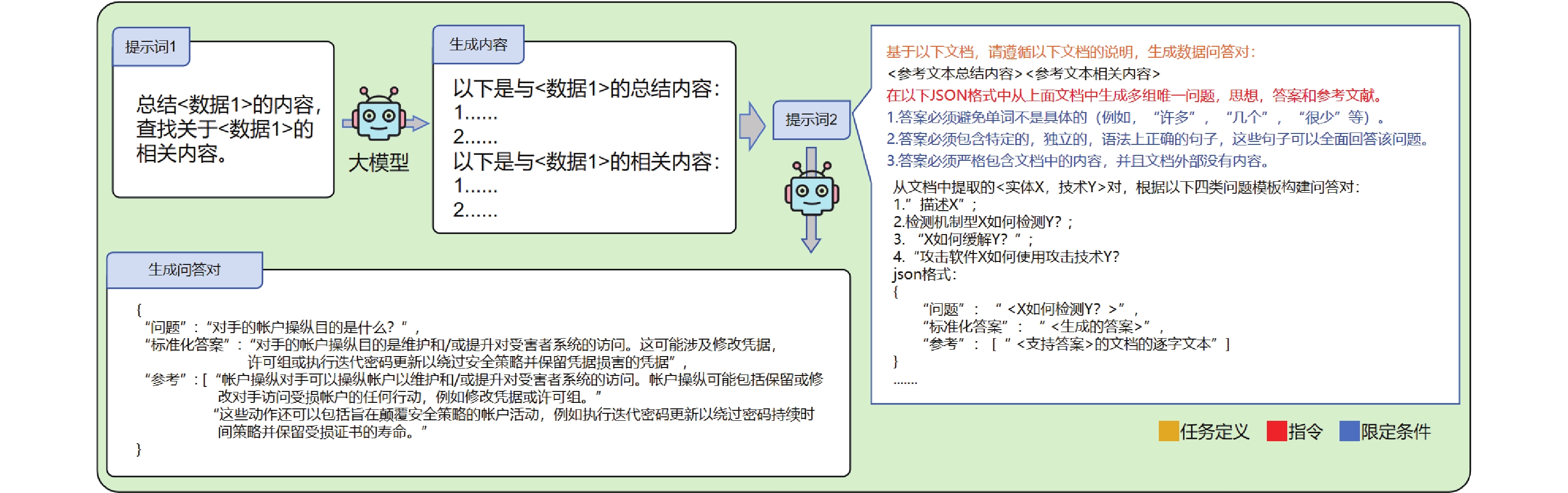
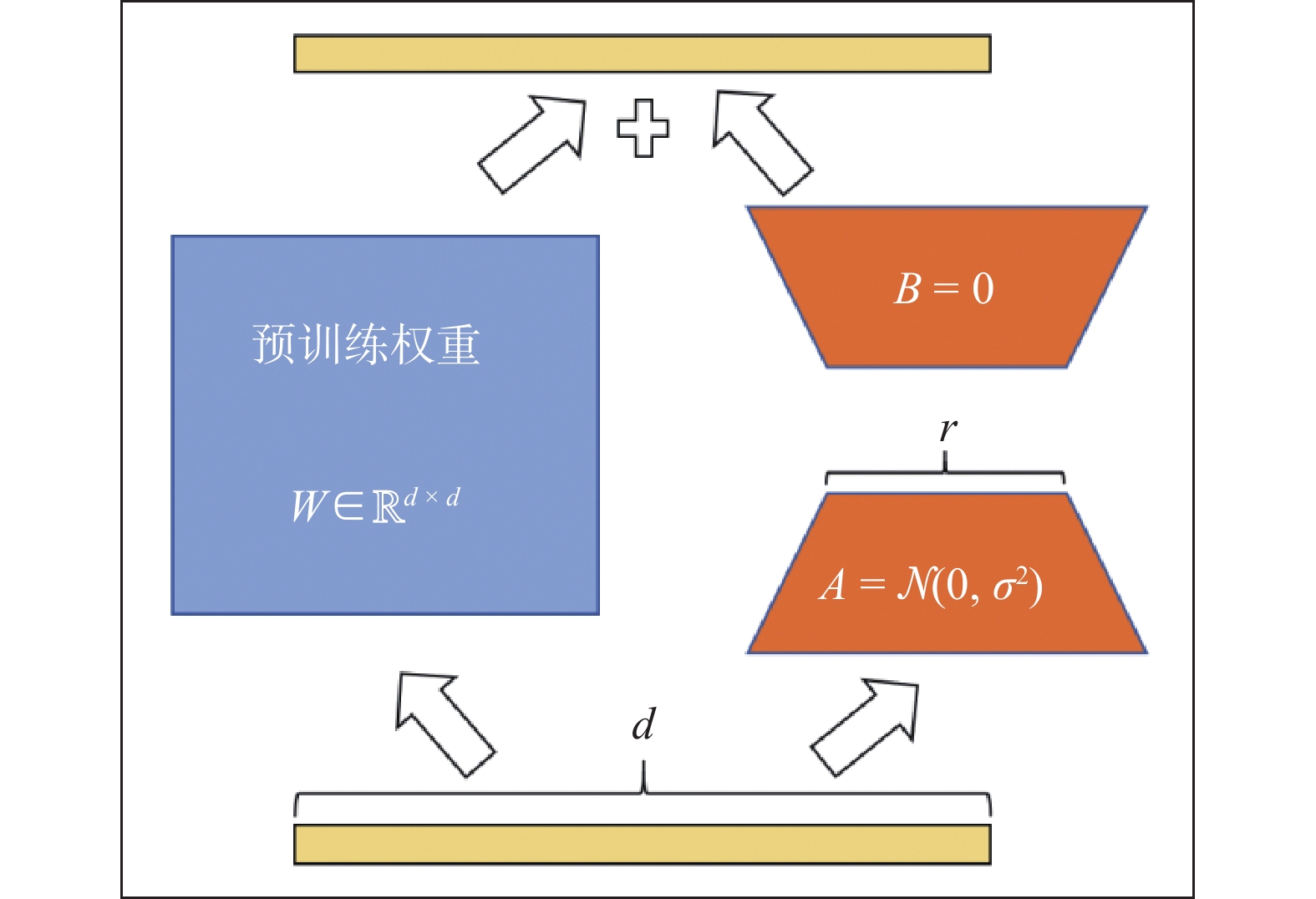
Figure/Table detail
LEAD-Cyber:a local fine-tuned vertical domain LLMs for cybersecurity with open-source LLMs and full-cycle training datasets
Journal of Cybersecurity,
DOI: 10.20172/j.issn.2097-3136.250116
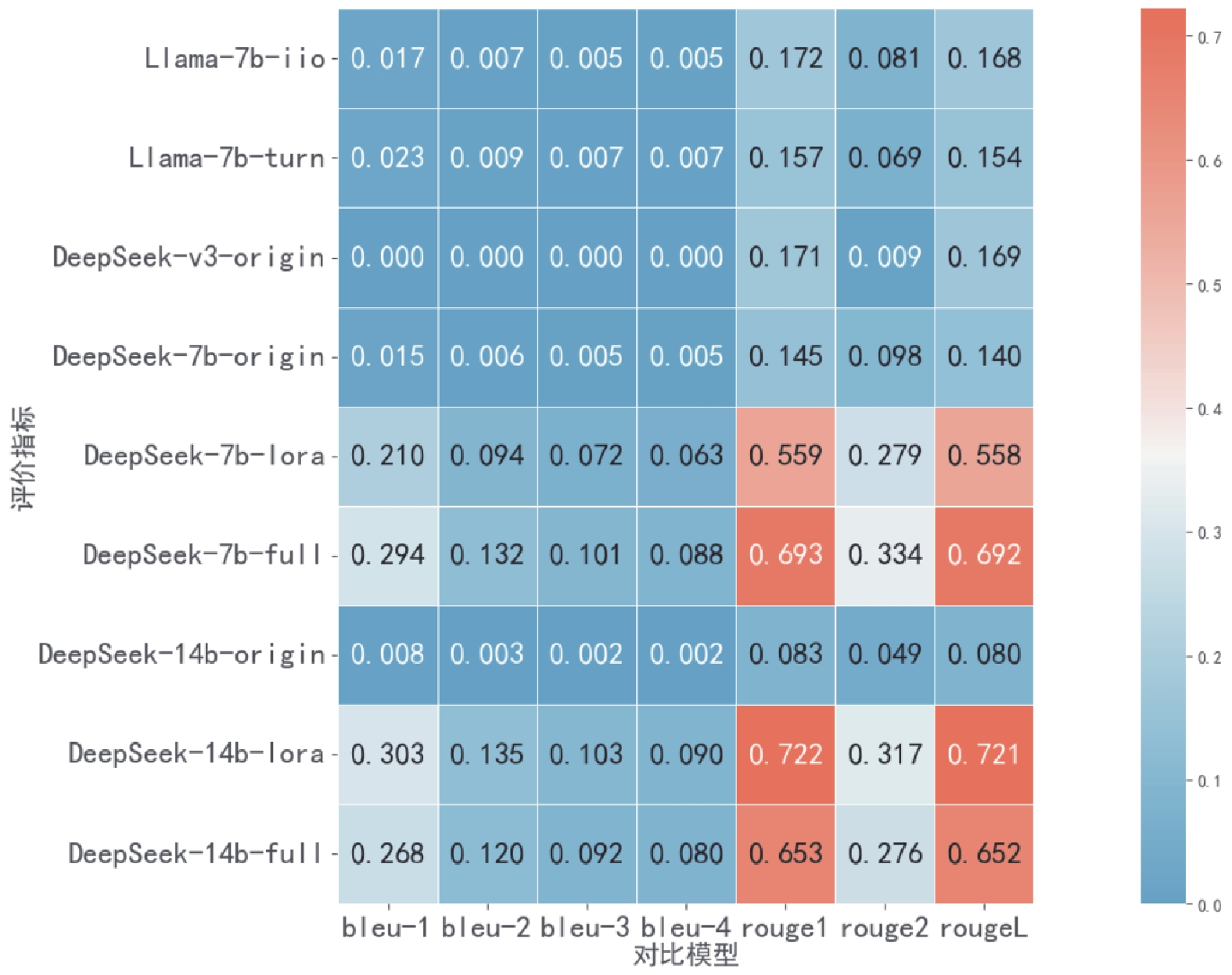
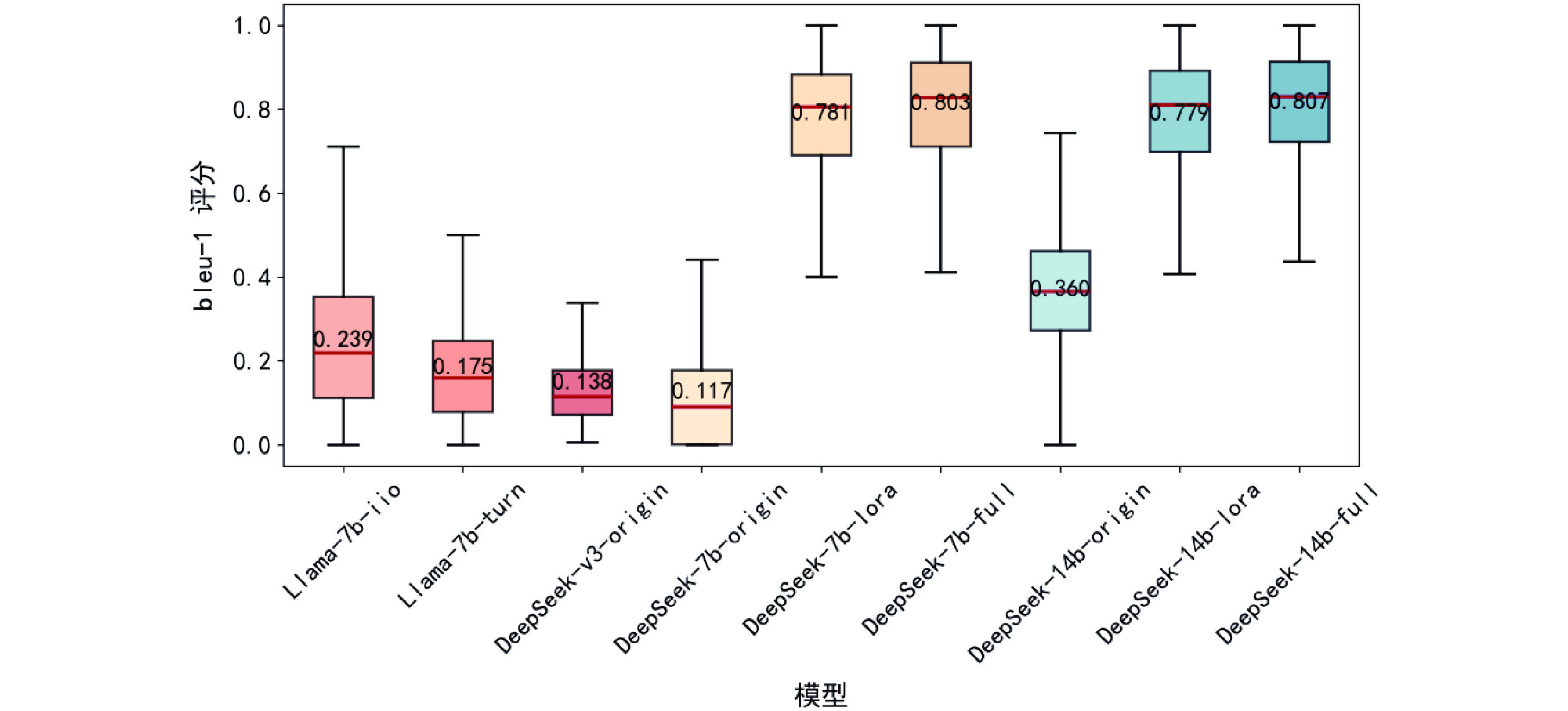
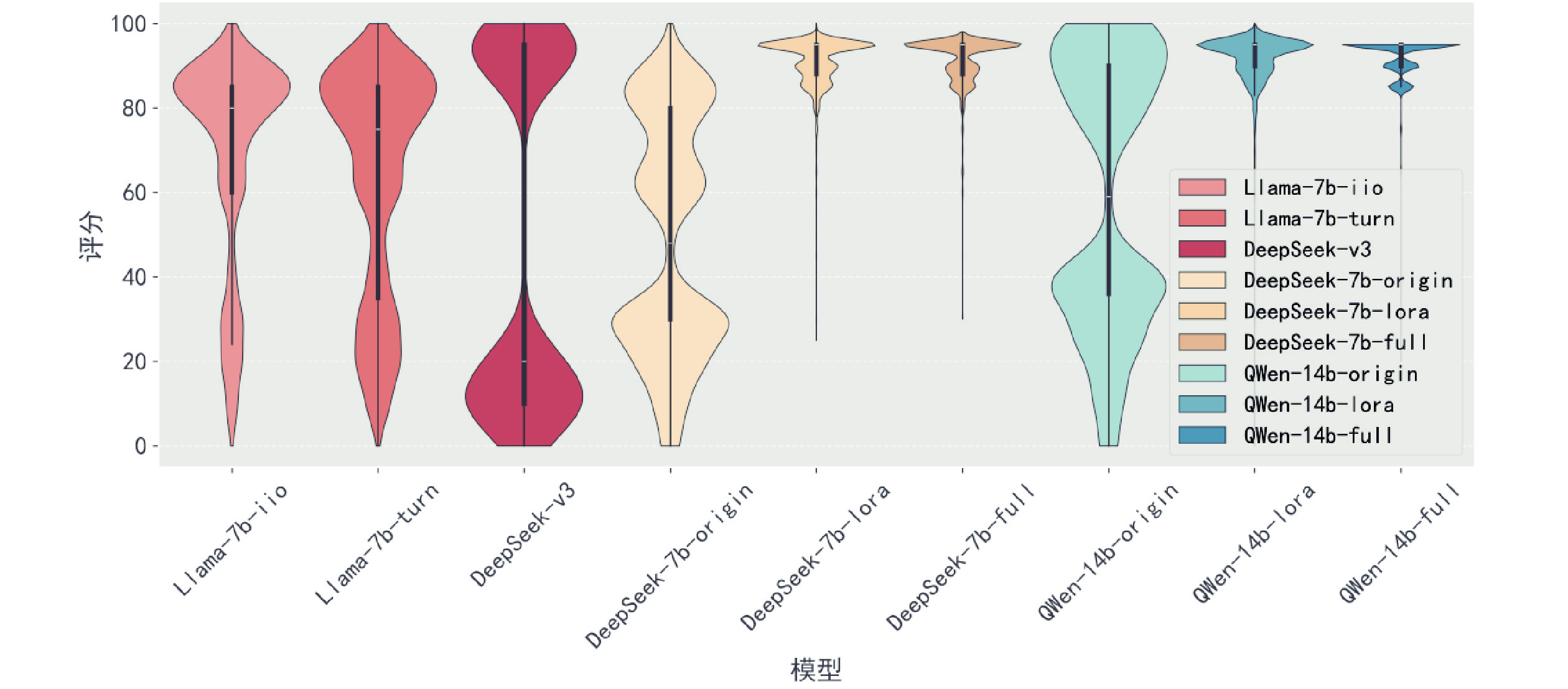
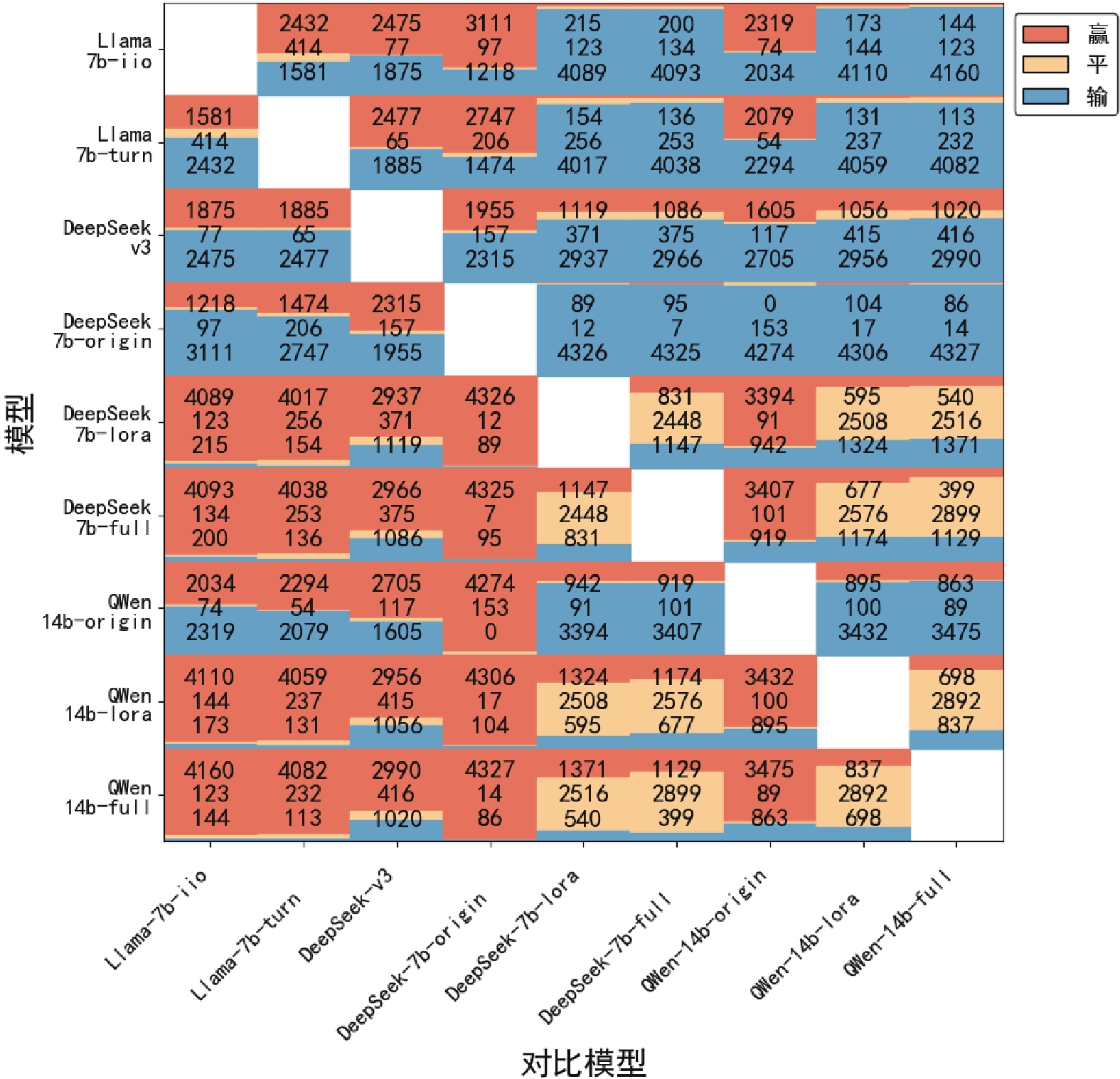
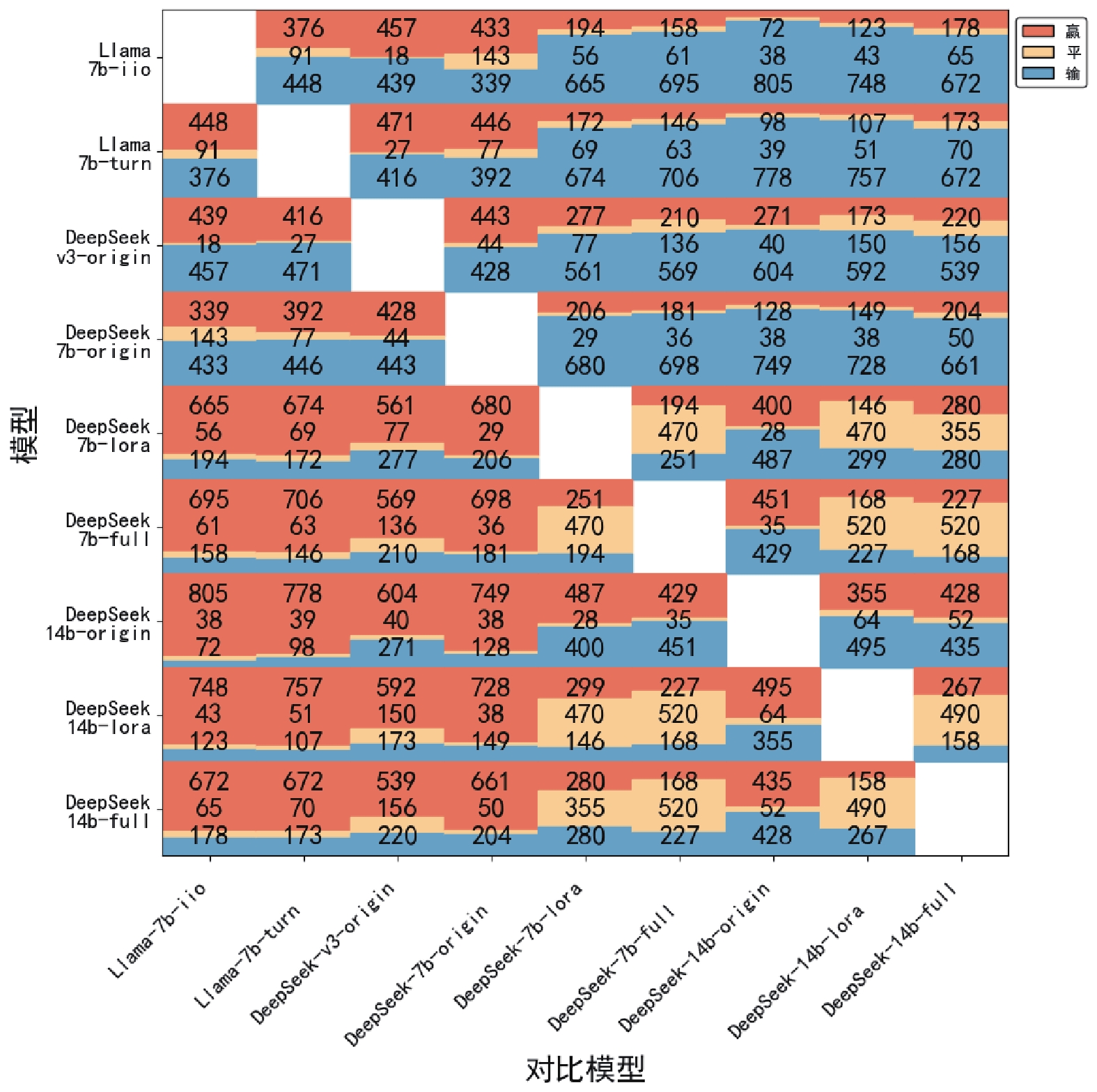
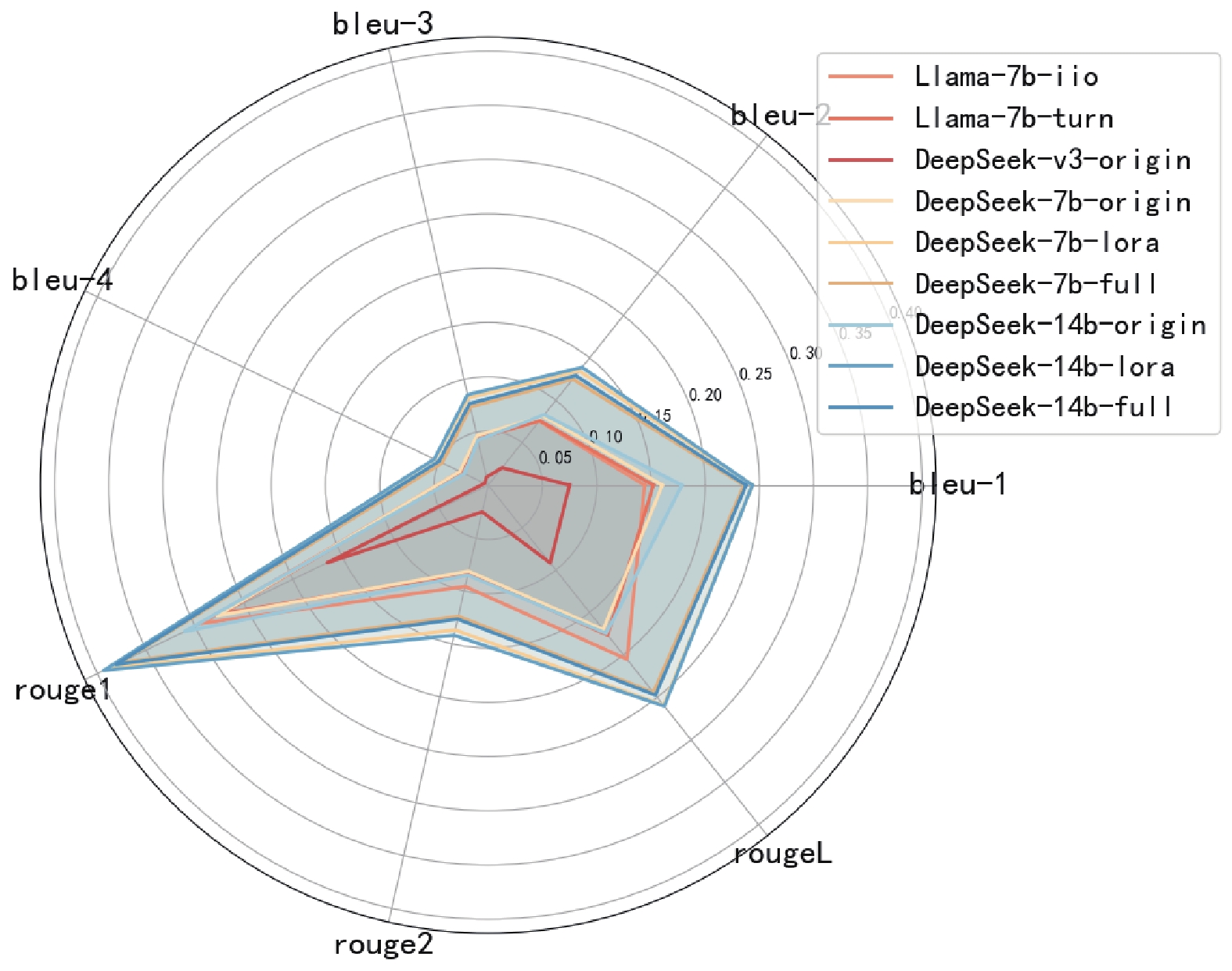
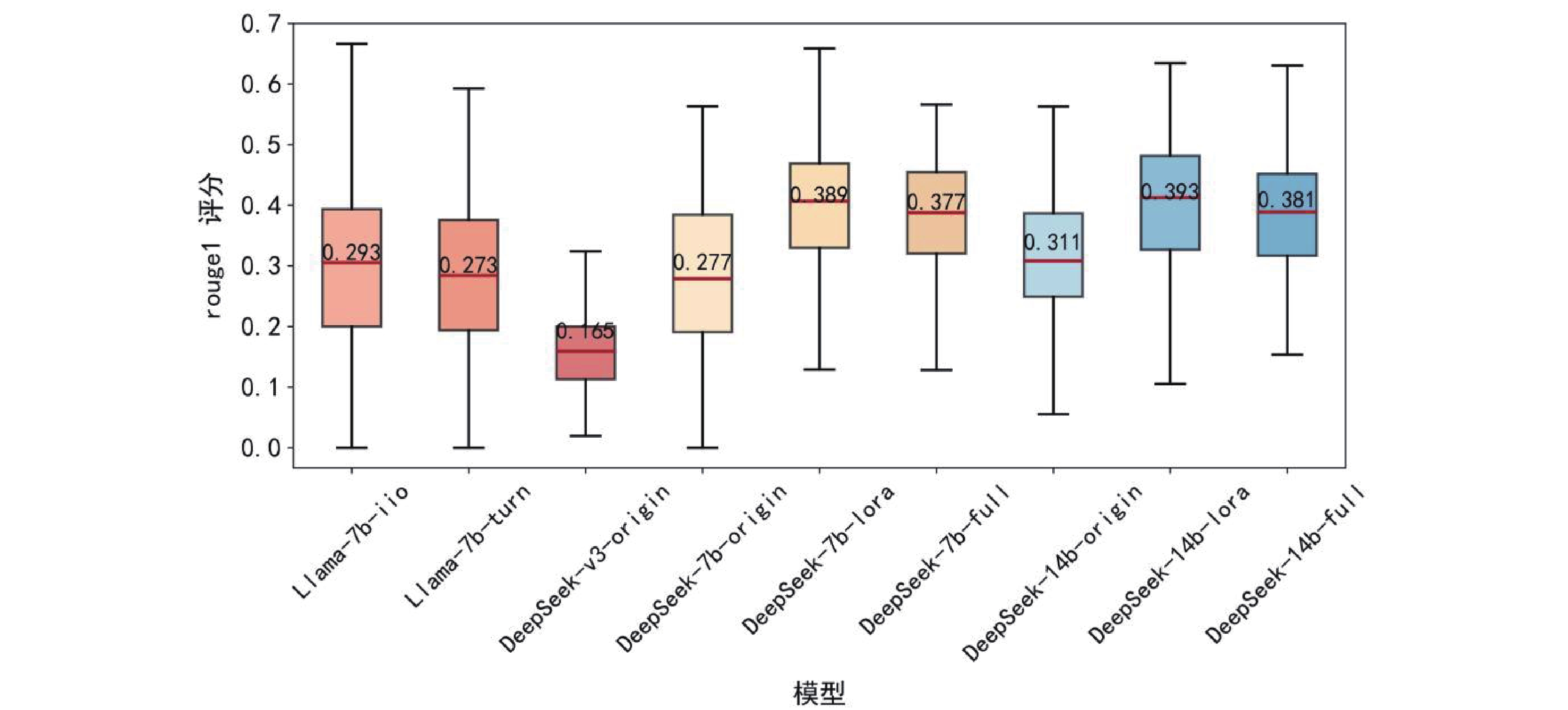
Fig.9 Rouge-L on experimental results on CTI-Bench
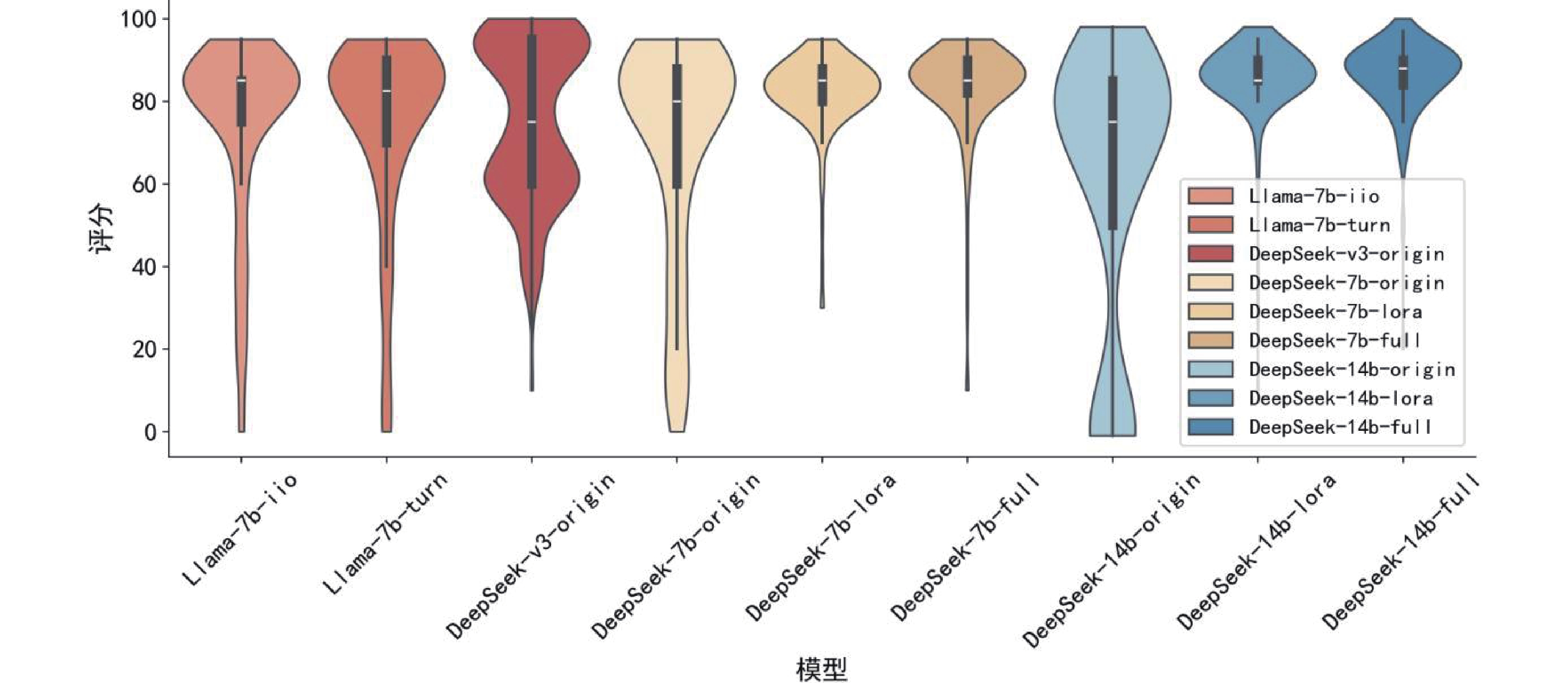
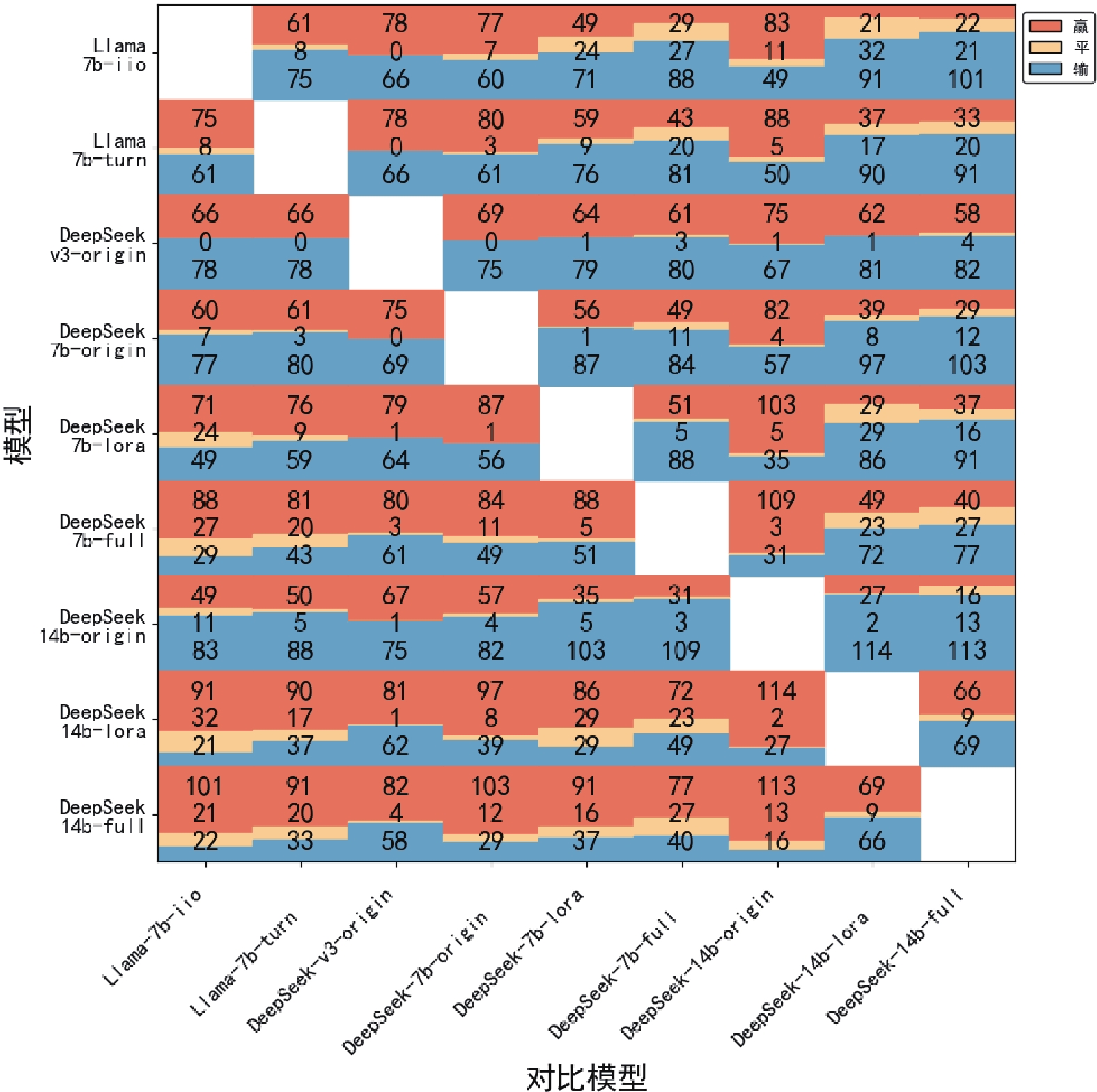
Other figure/table from this article