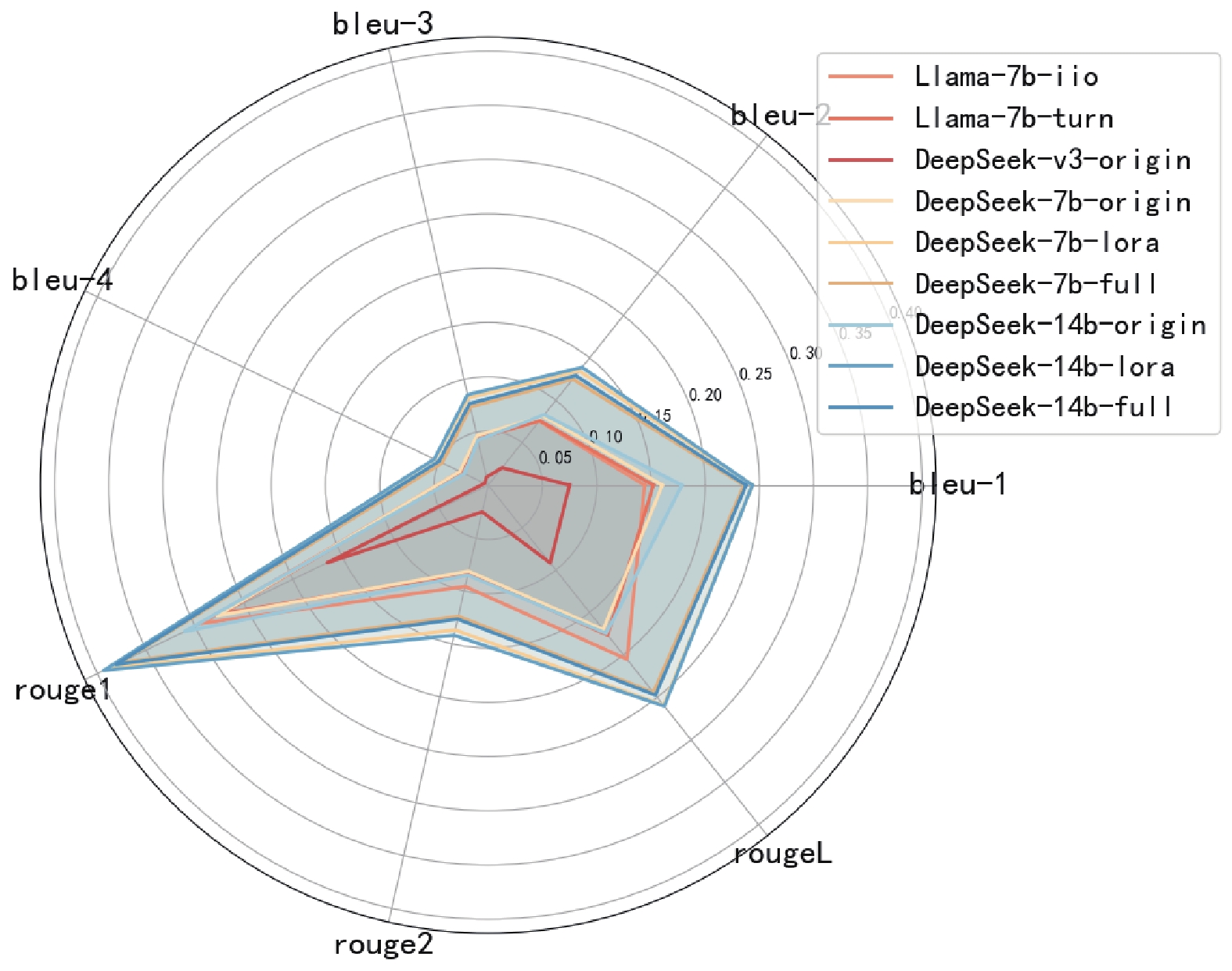
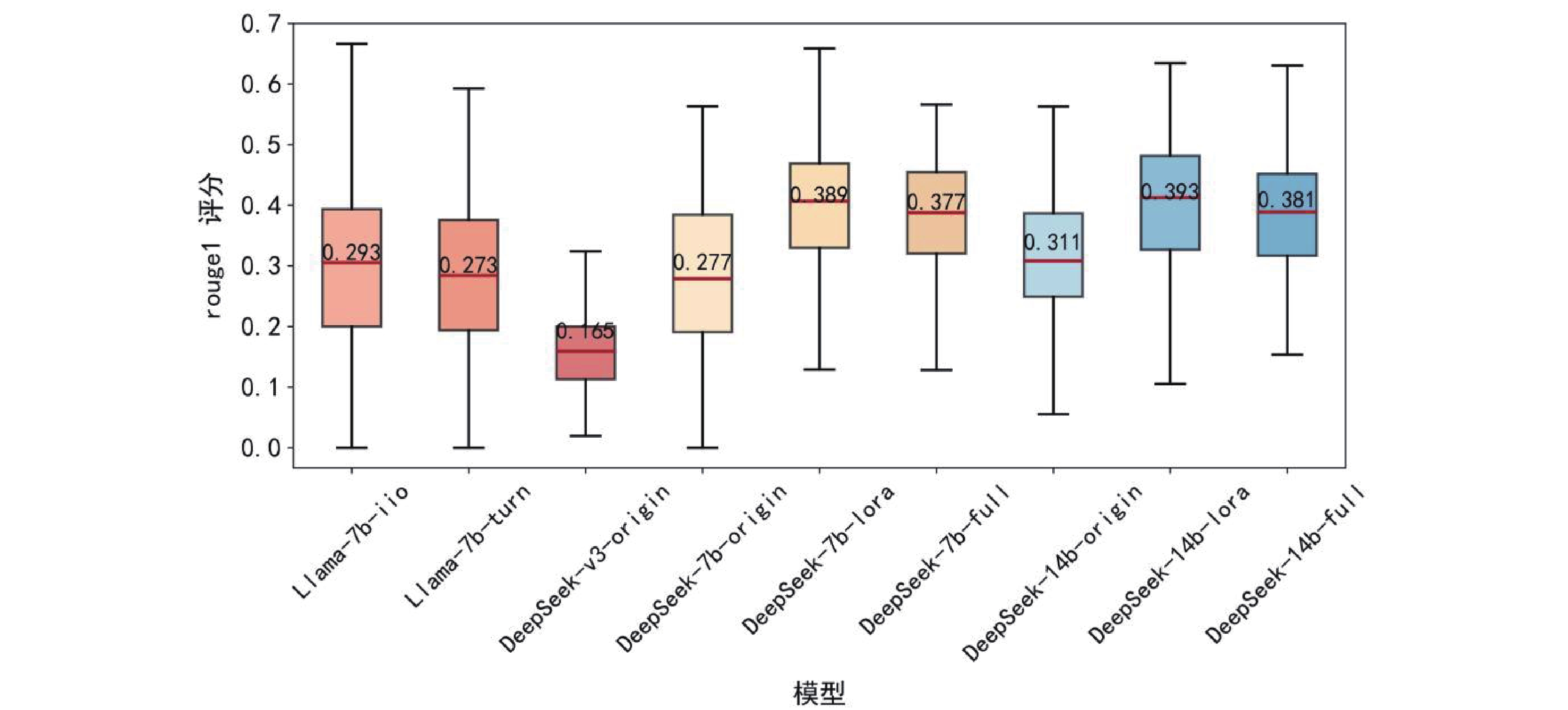
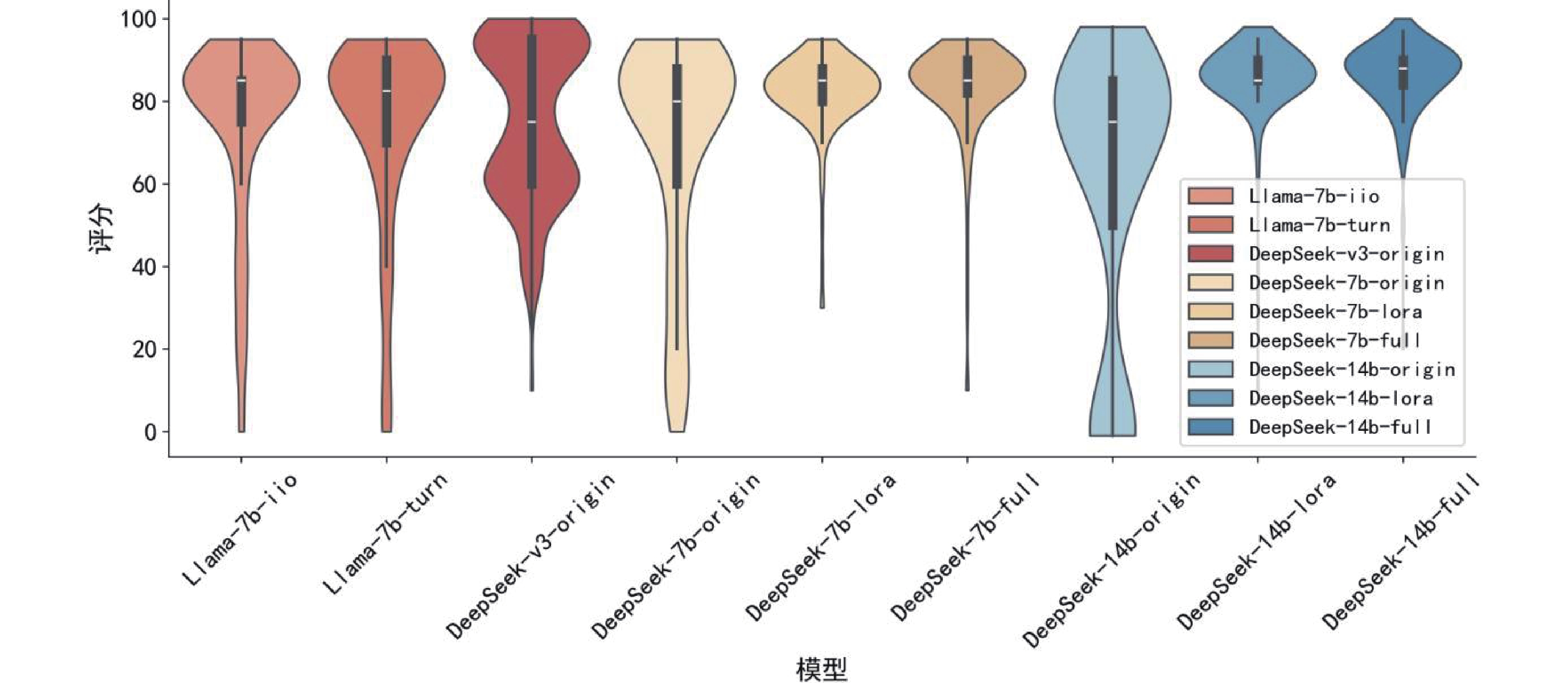
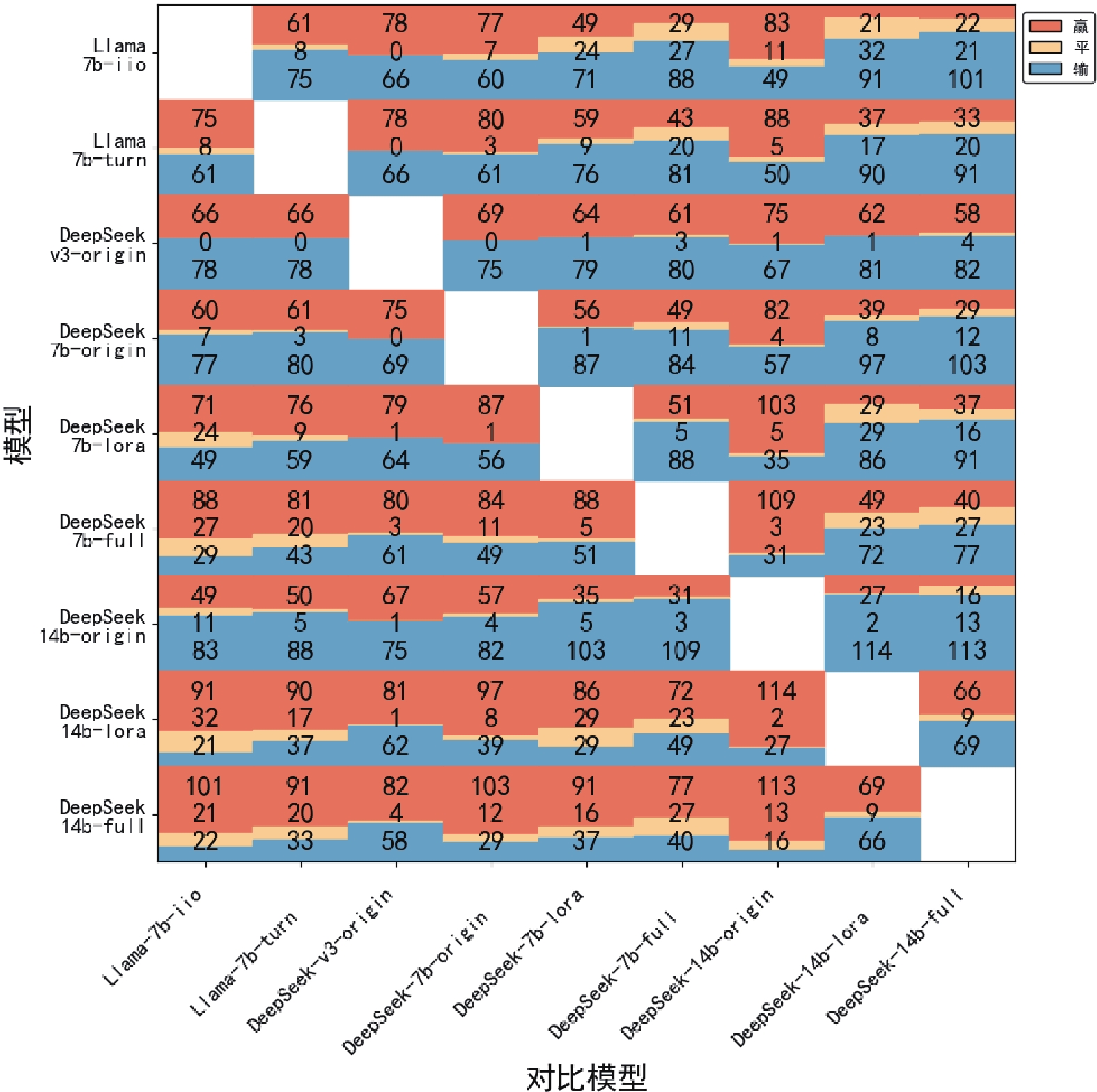
Figure/Table detail
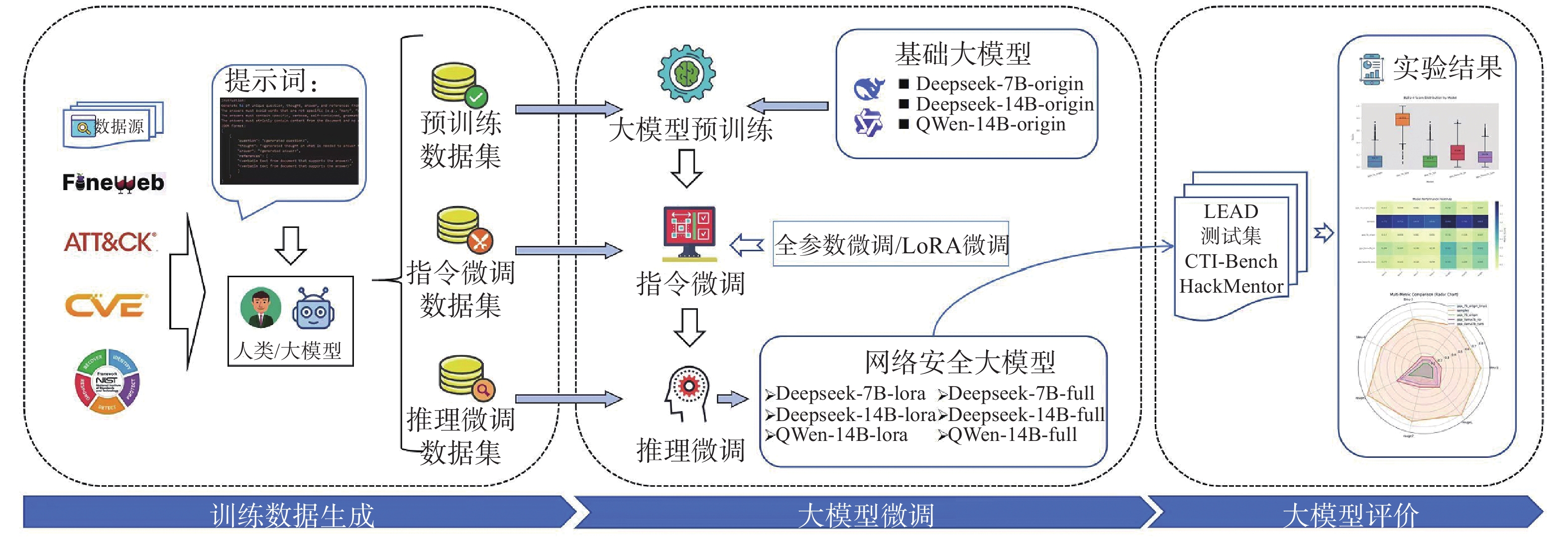
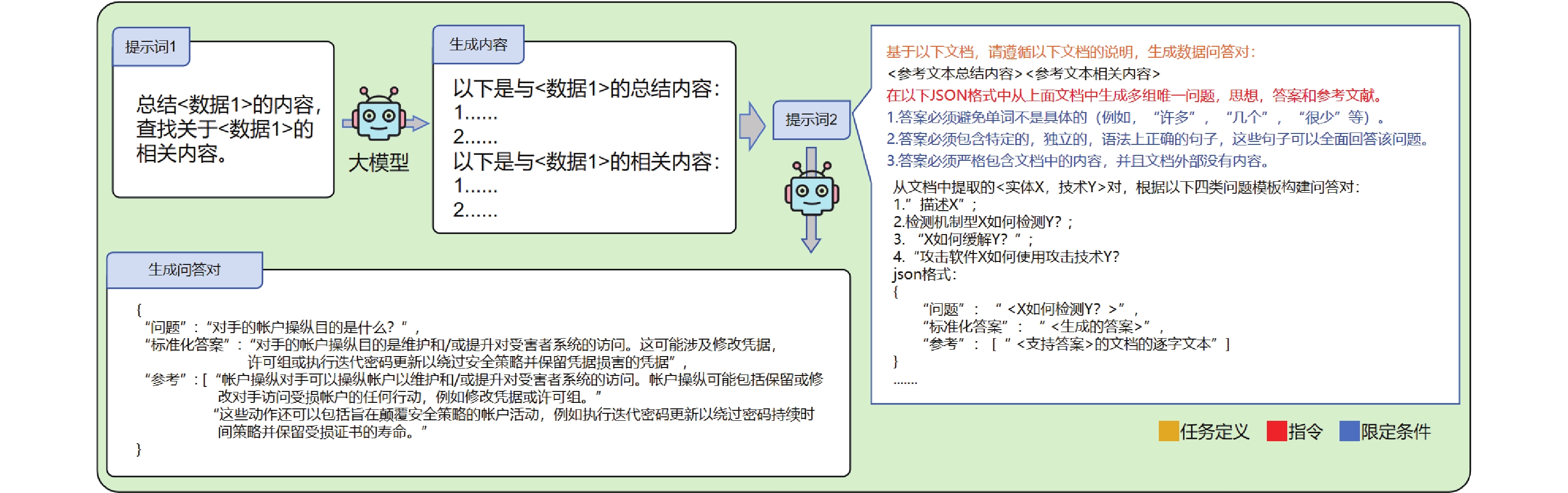
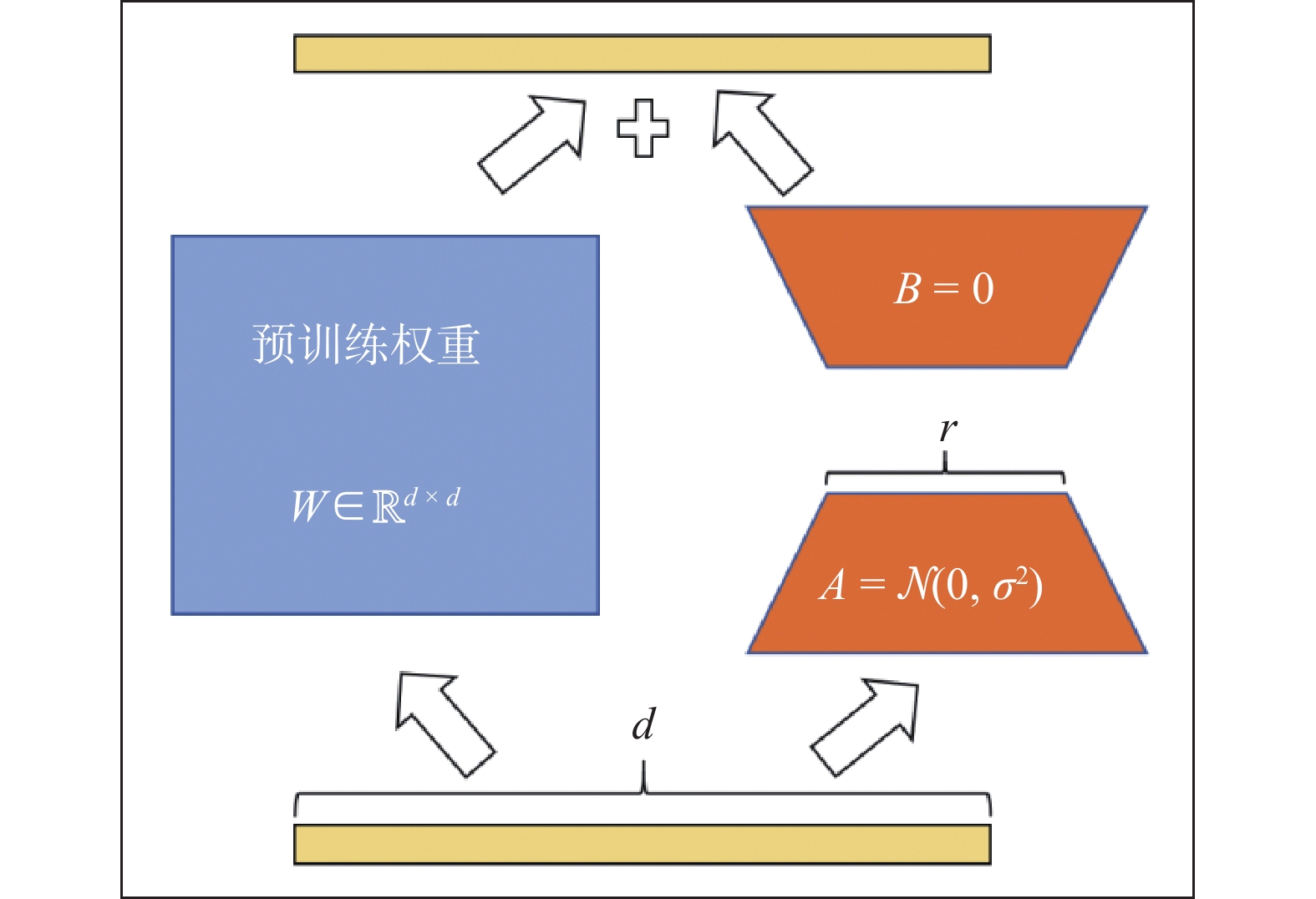
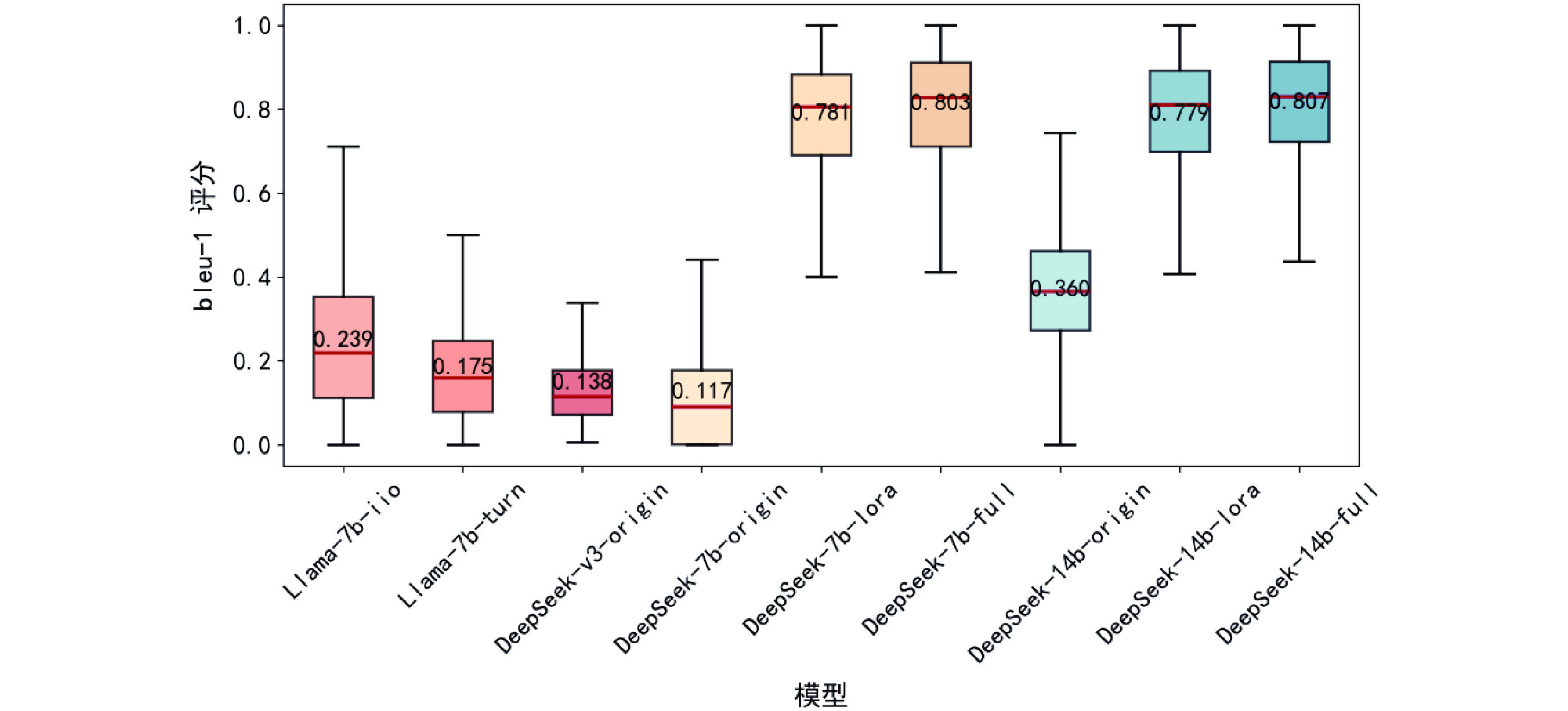
LEAD-Cyber:a local fine-tuned vertical domain LLMs for cybersecurity with open-source LLMs and full-cycle training datasets
Journal of Cybersecurity,
DOI: 10.20172/j.issn.2097-3136.250116
| 任务名称 | 解决要求 |
| 根因映射 | 需理解漏洞机制,推断根本原因而非字面匹配 |
| 漏洞威胁预测 | 需推断攻击向量、影响范围等隐含信息 |
| 攻击技术提取 | 需综合分散信息识别战术、技术和程序 |
| 多项选择题 | 需理解威胁识别、检测策略、缓解技术等知识 |
Table 4 CTI-Bench Reasoning Task
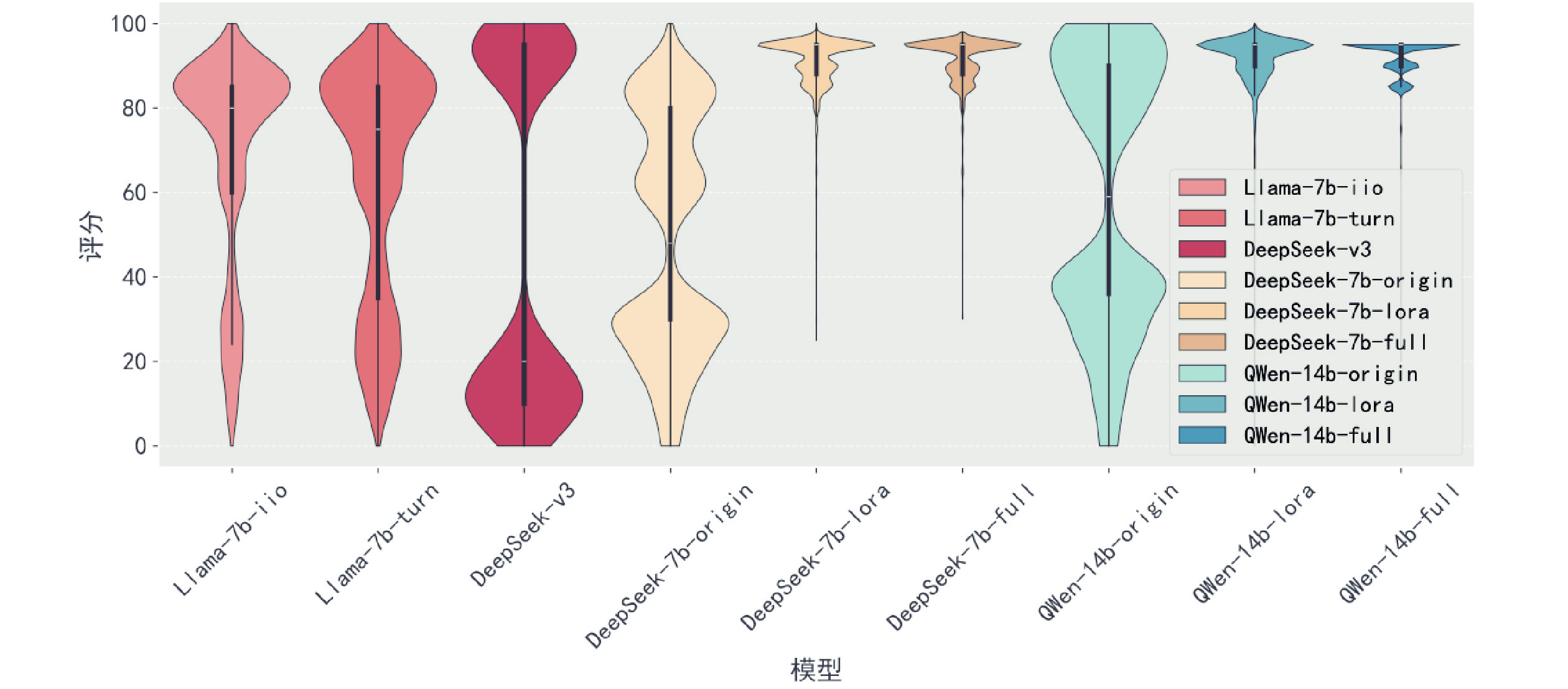
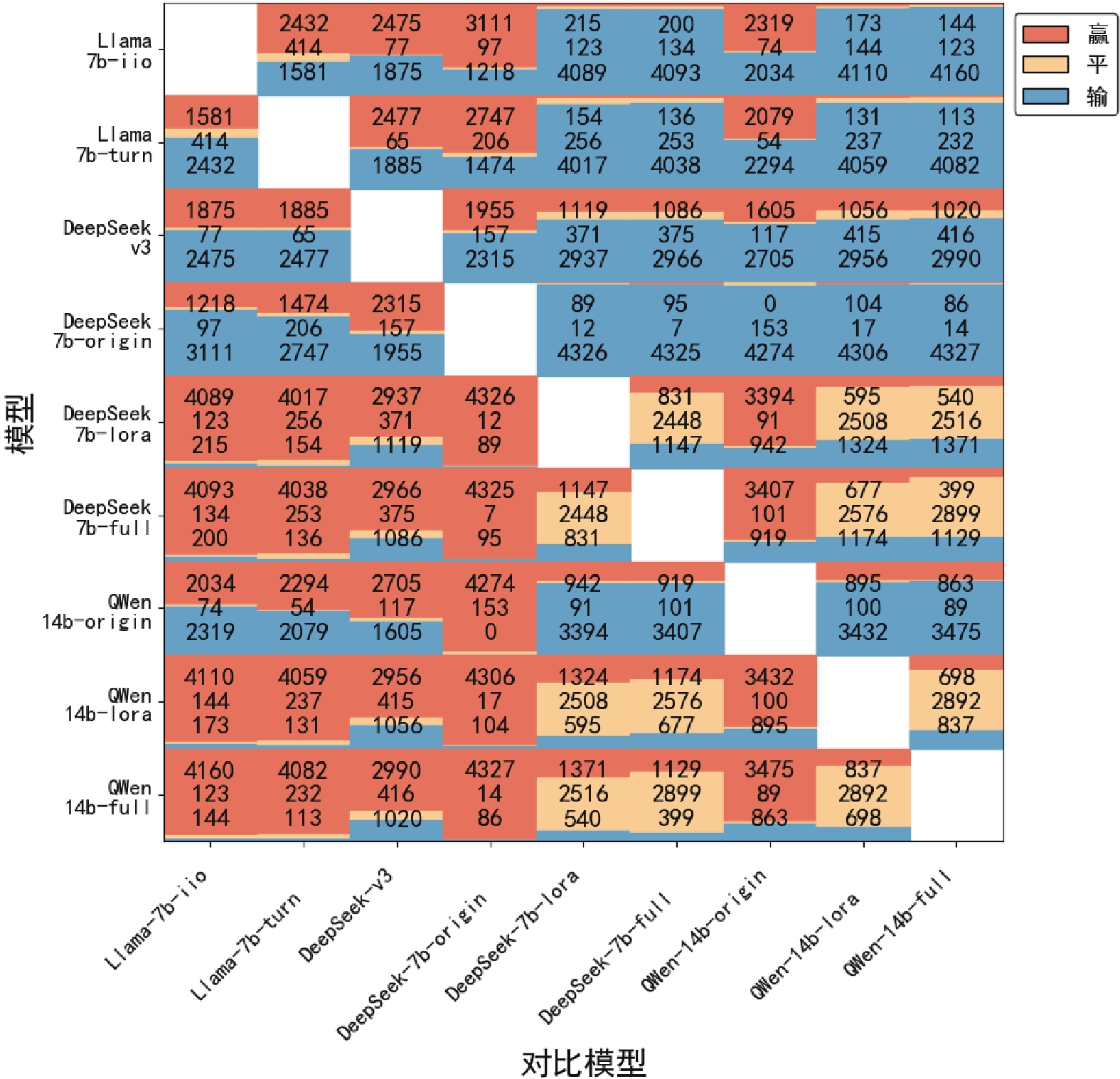
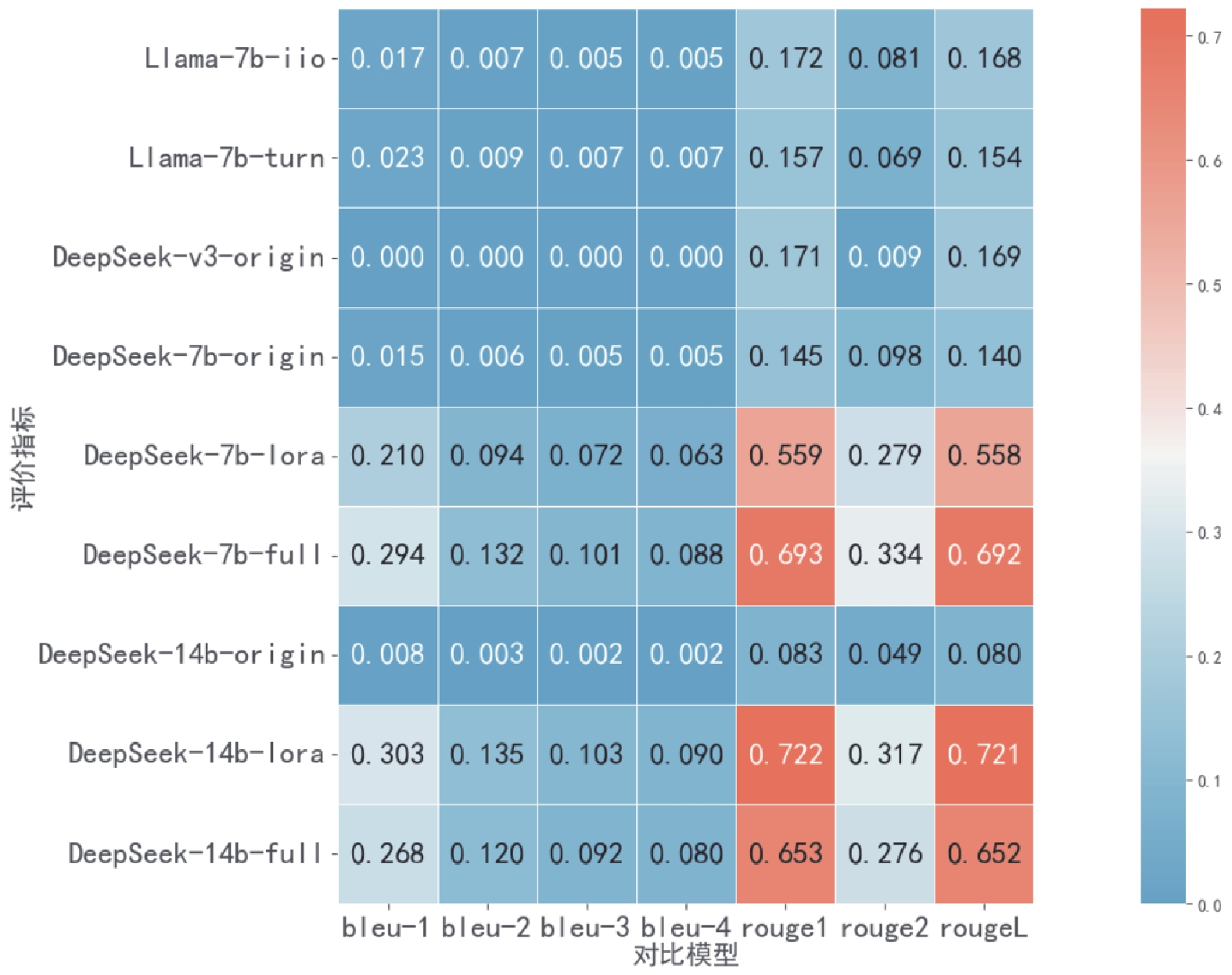
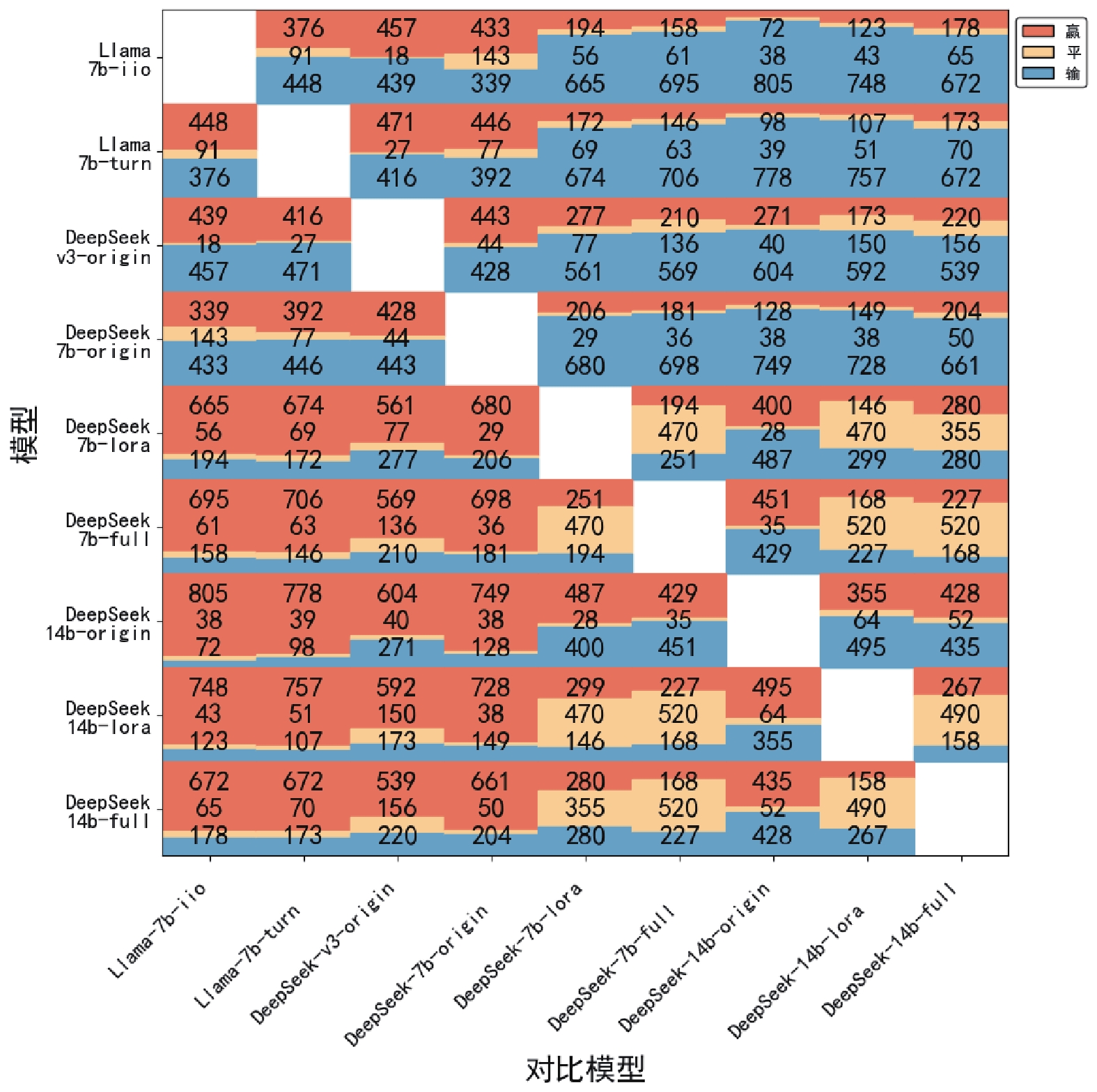
Other figure/table from this article