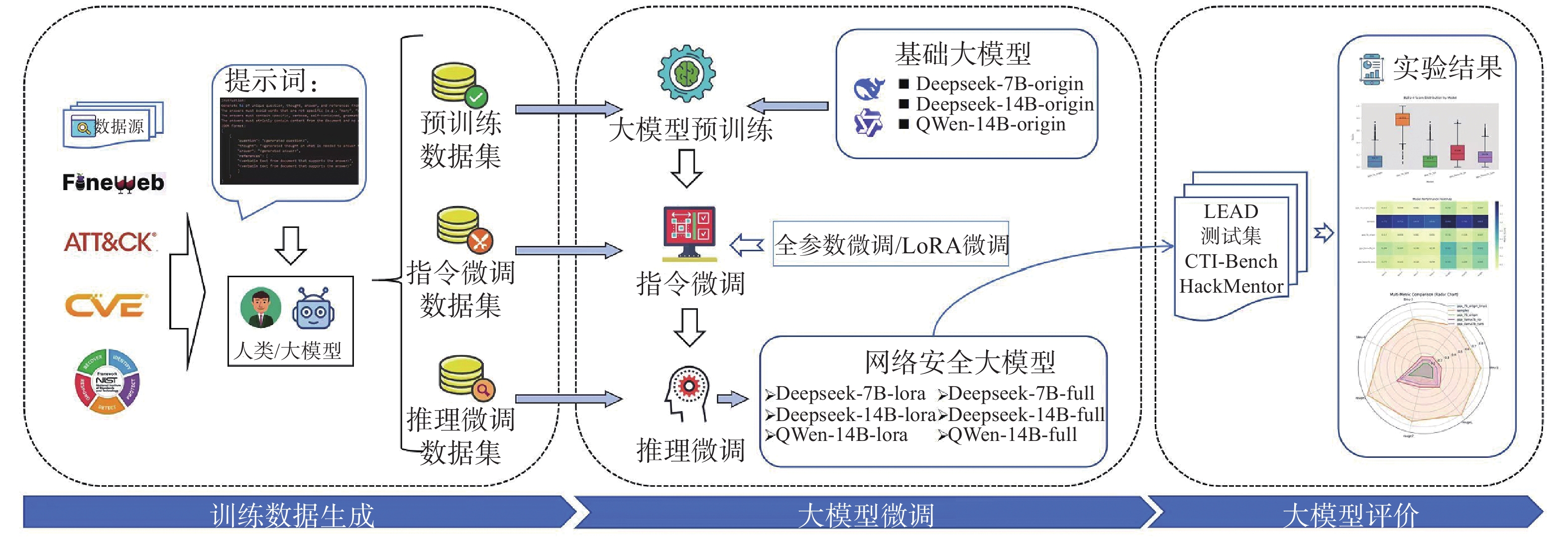
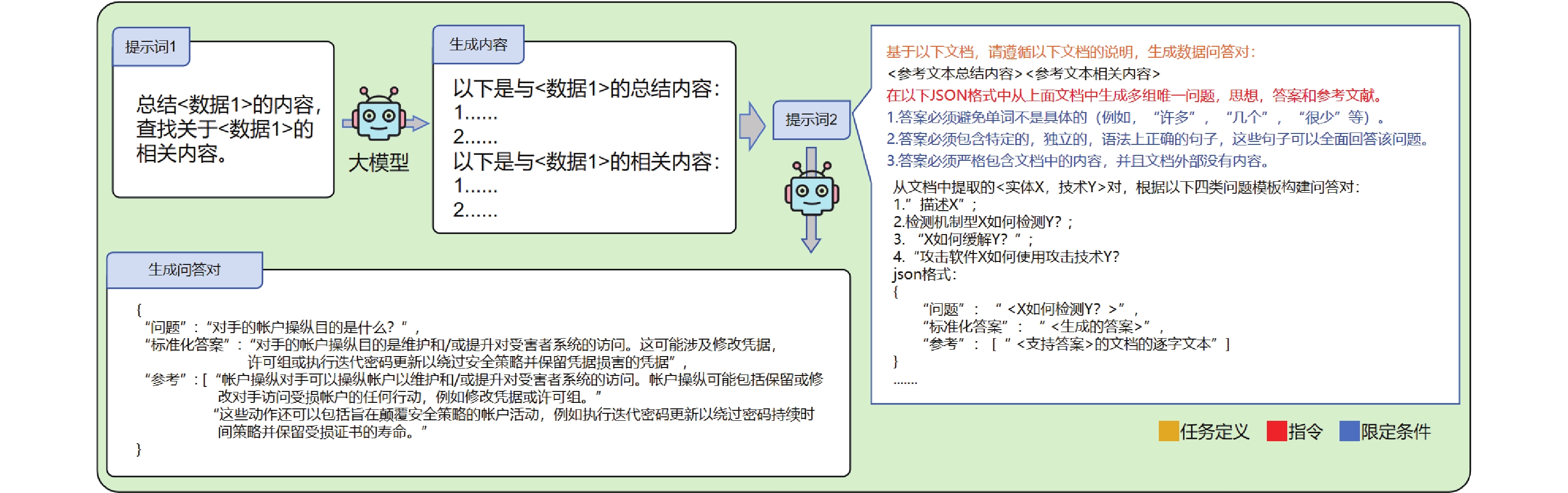
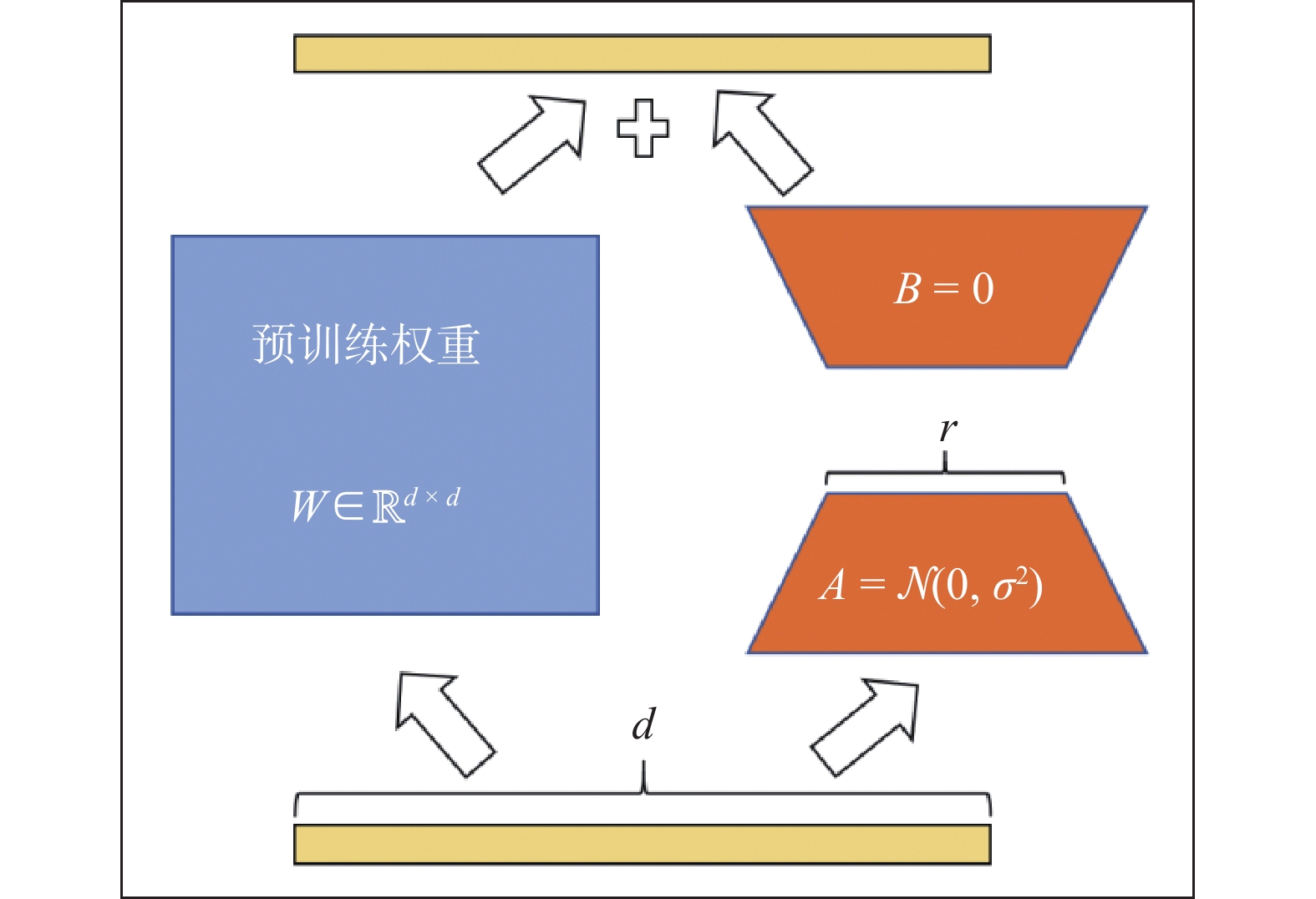
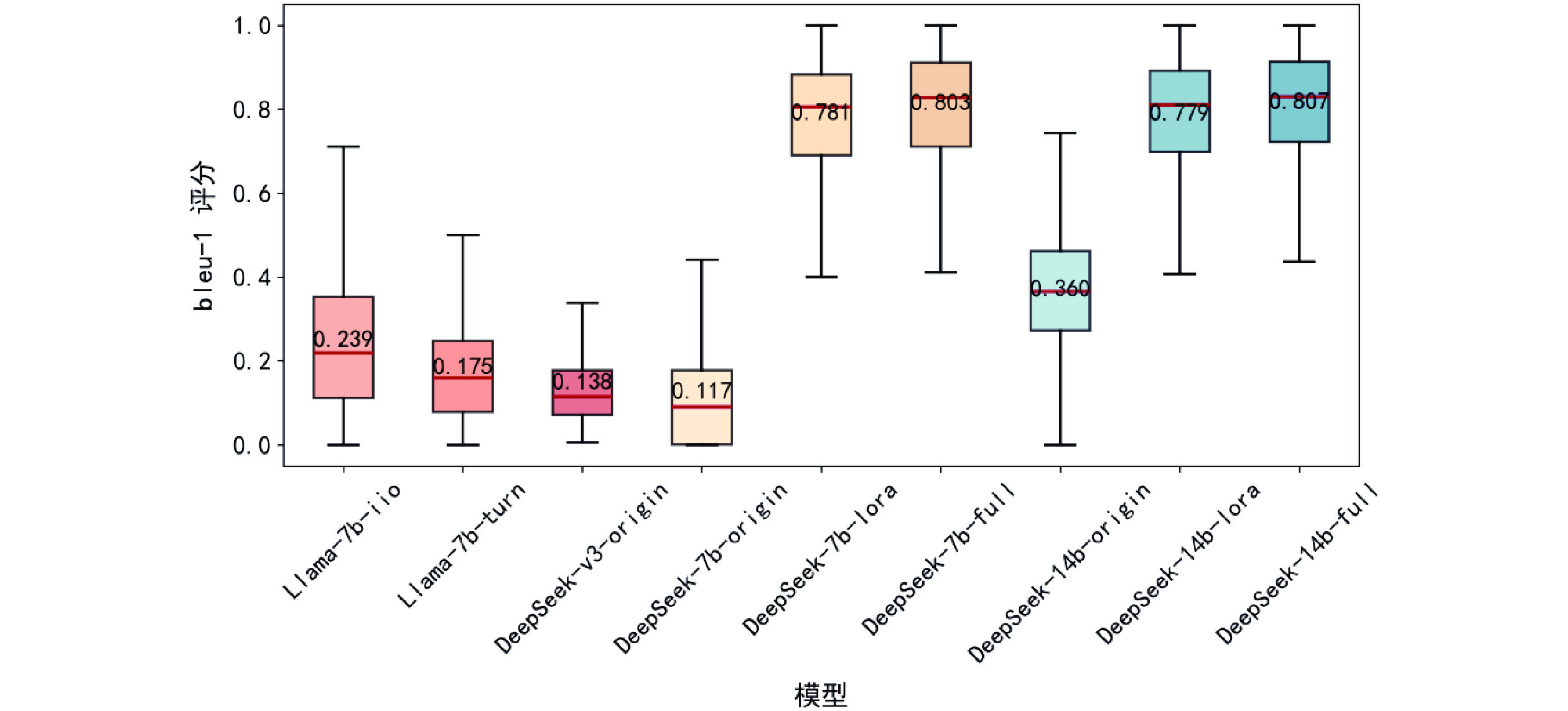
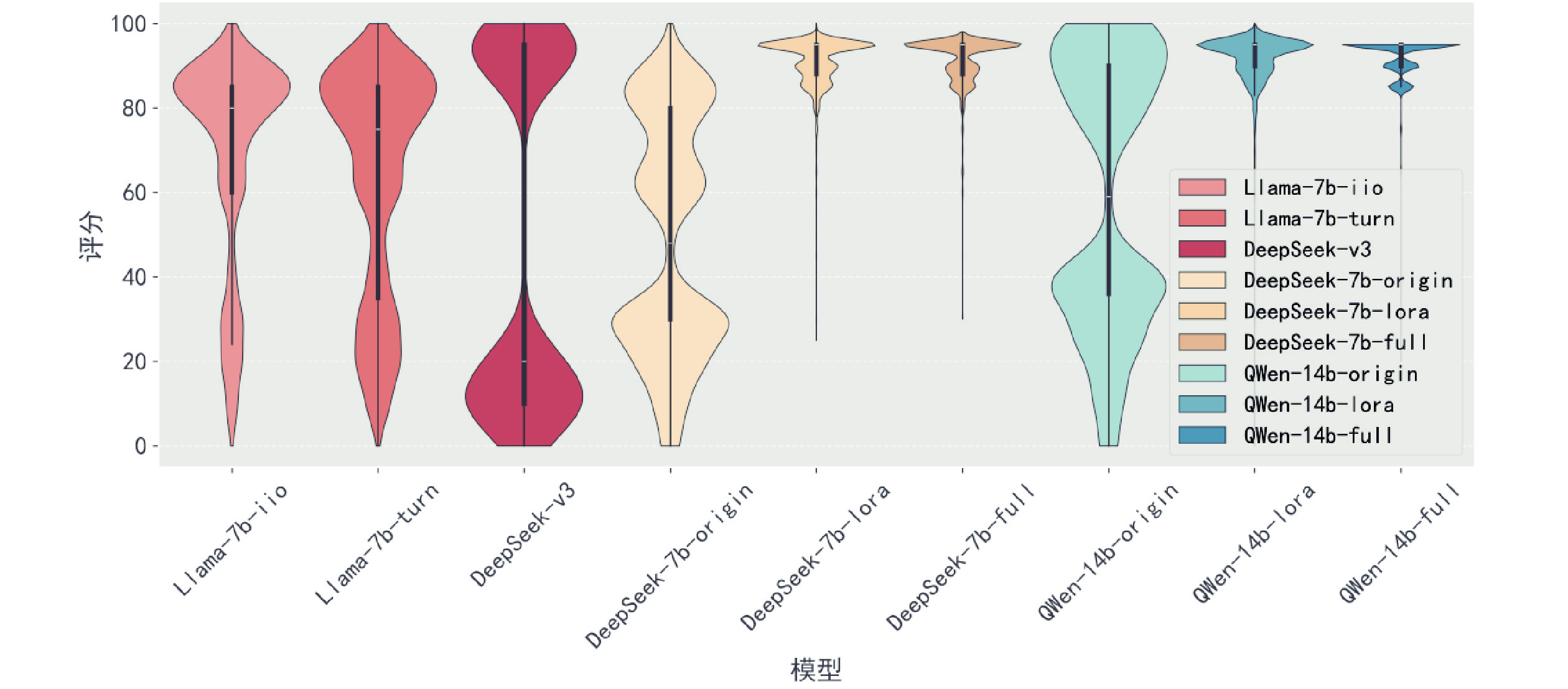
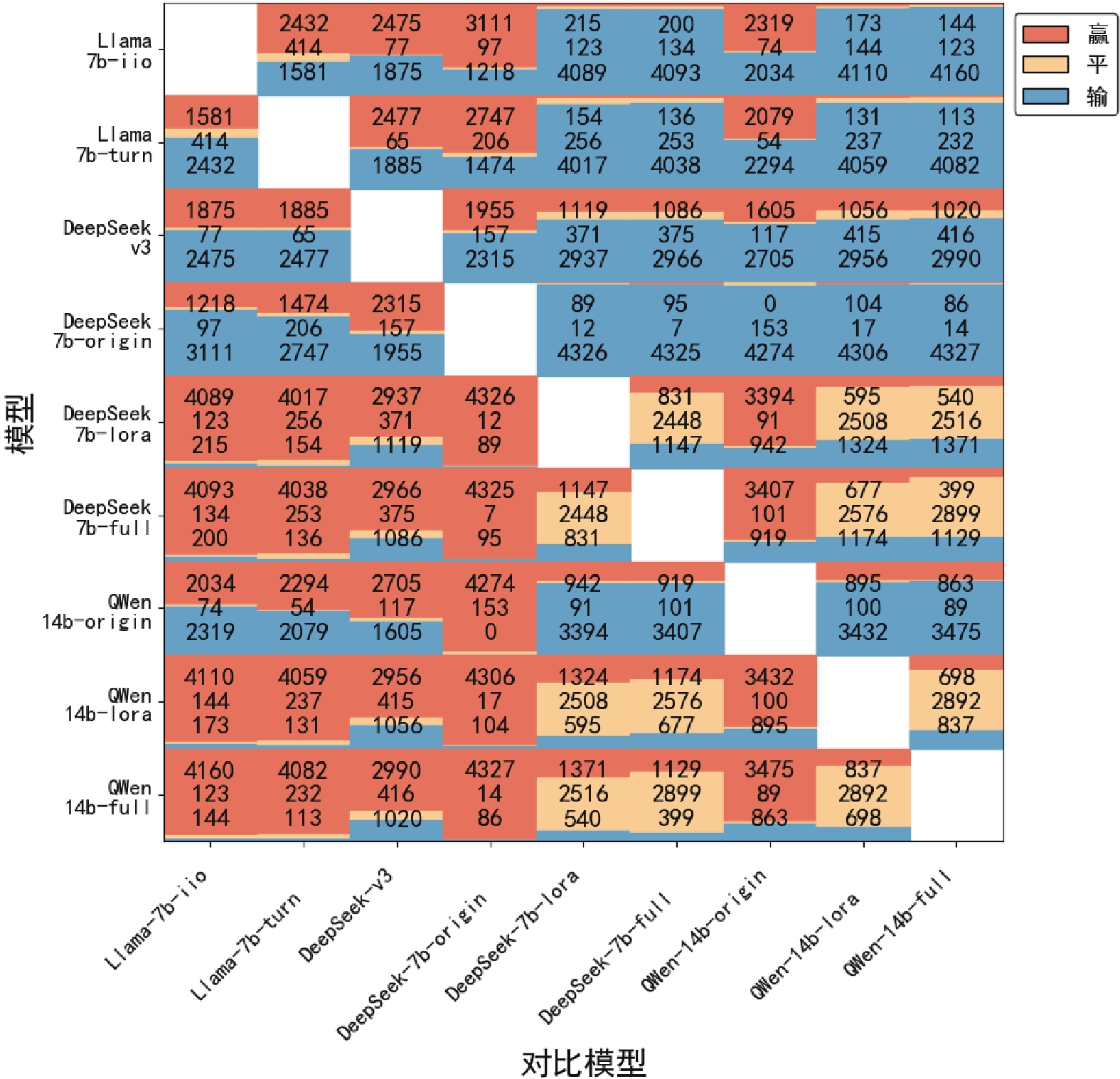
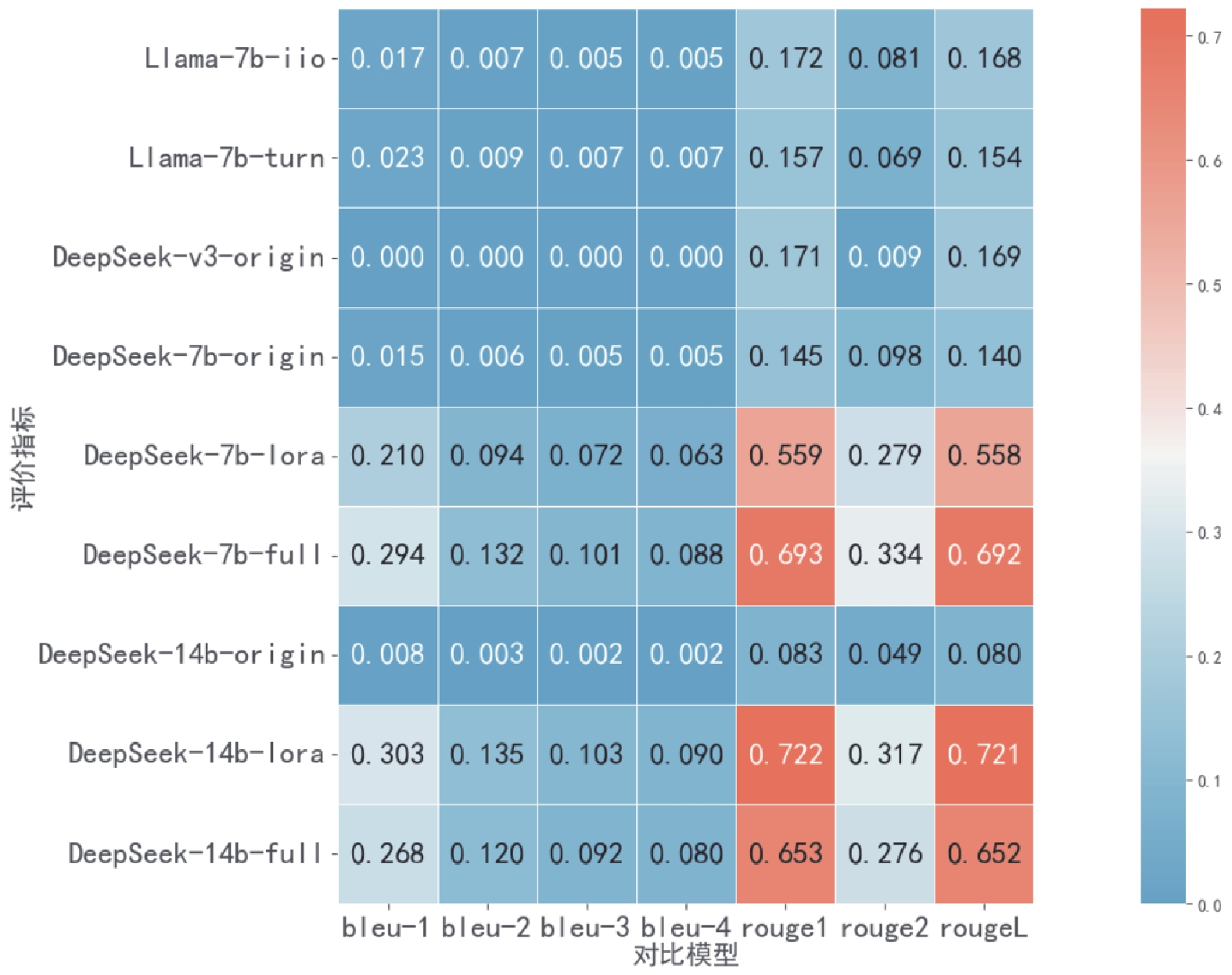
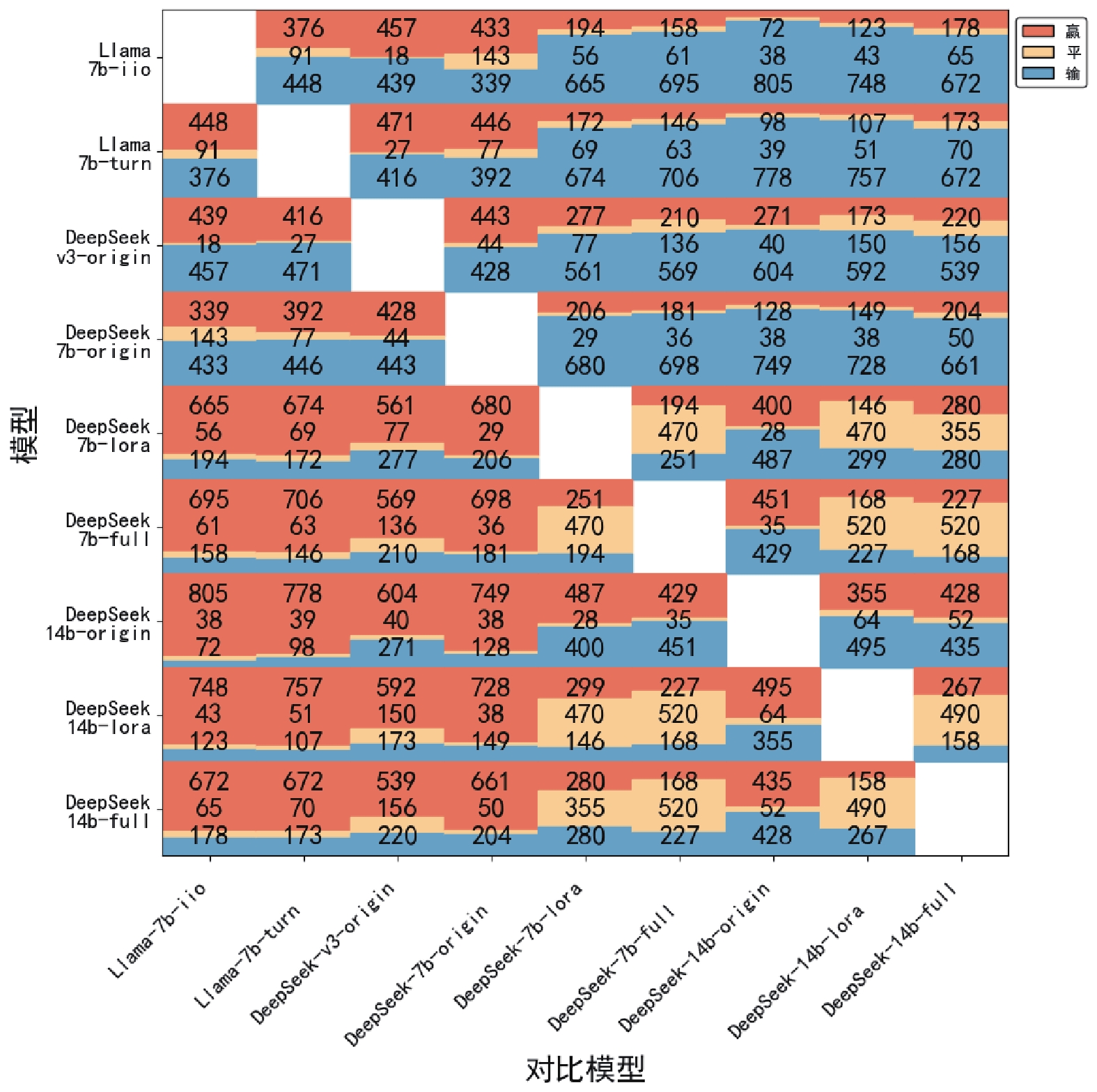
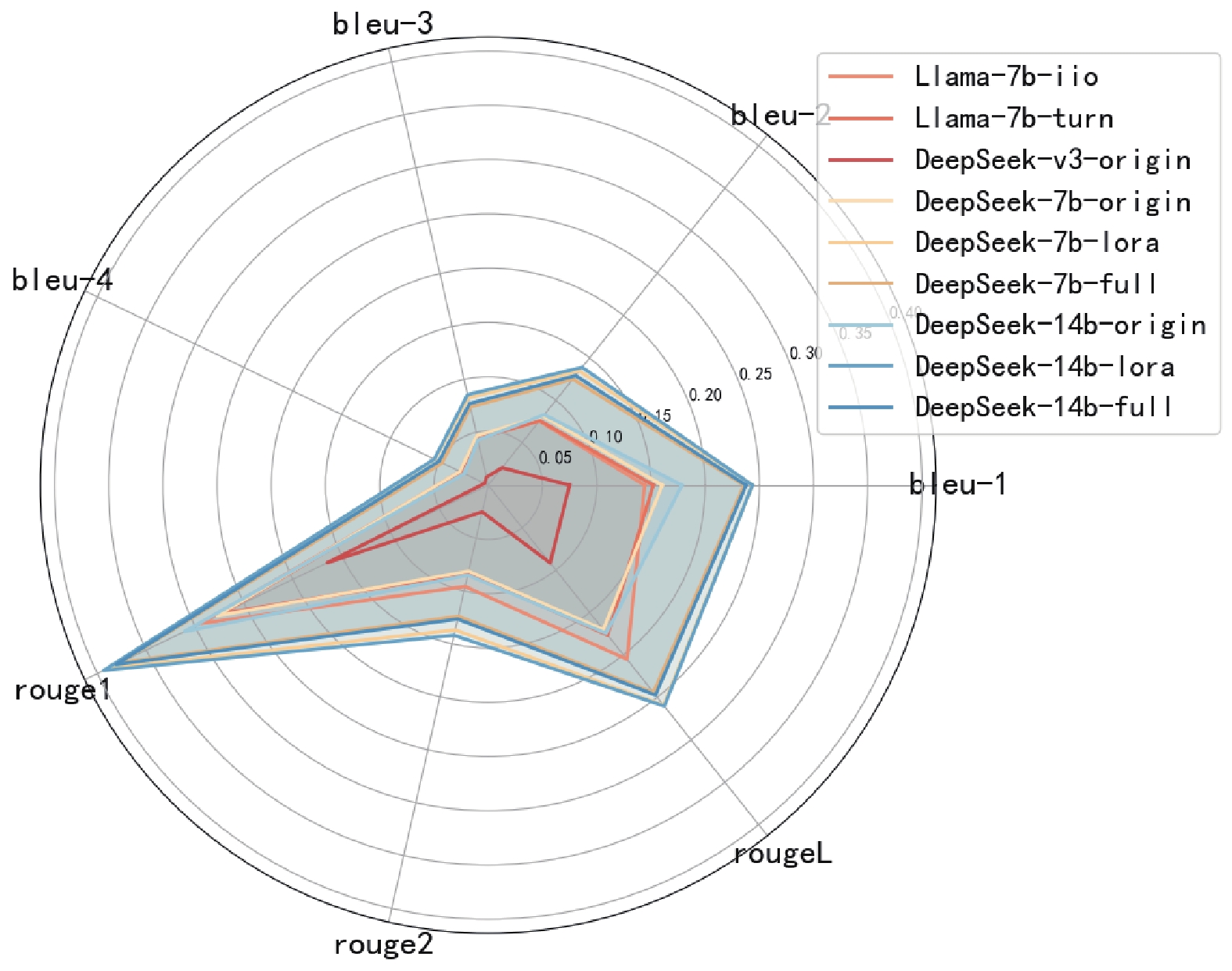
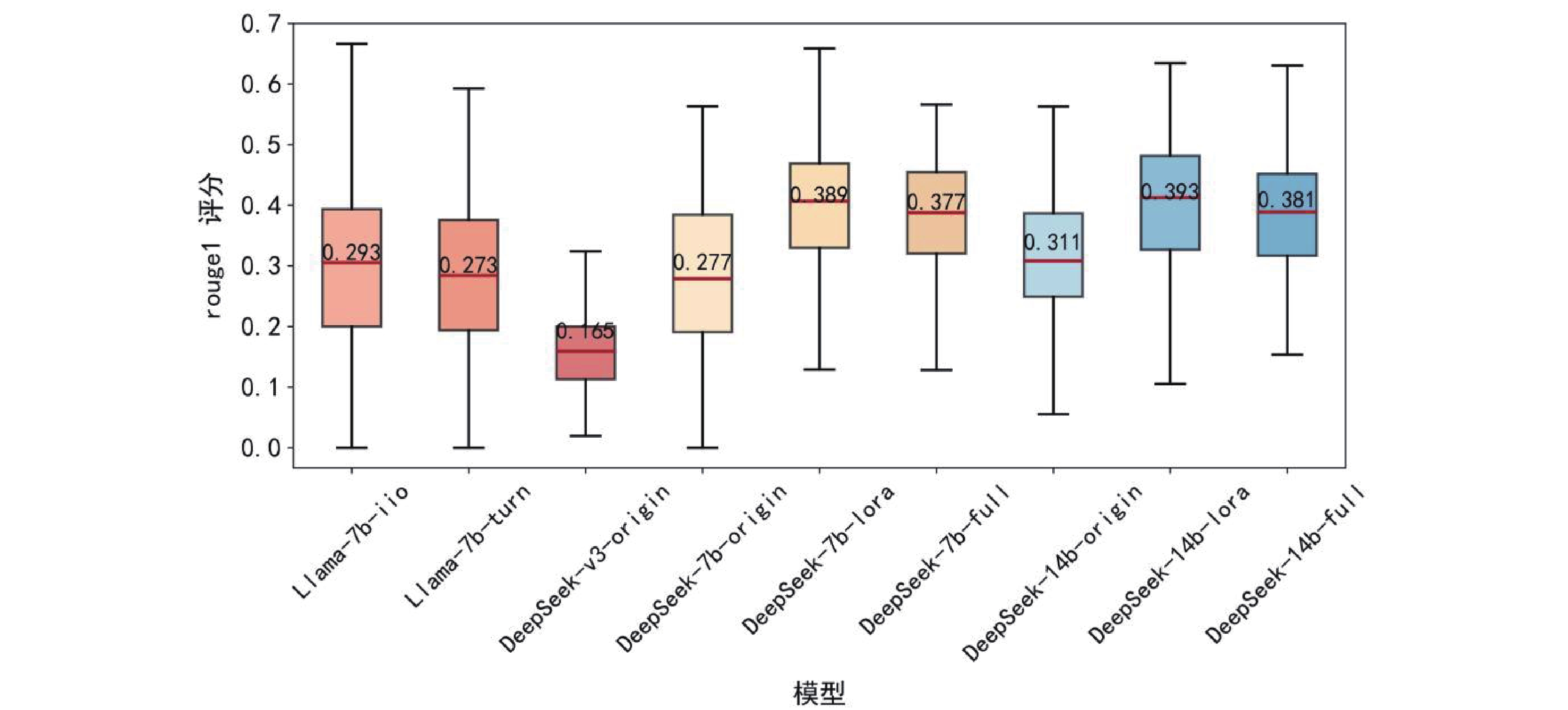
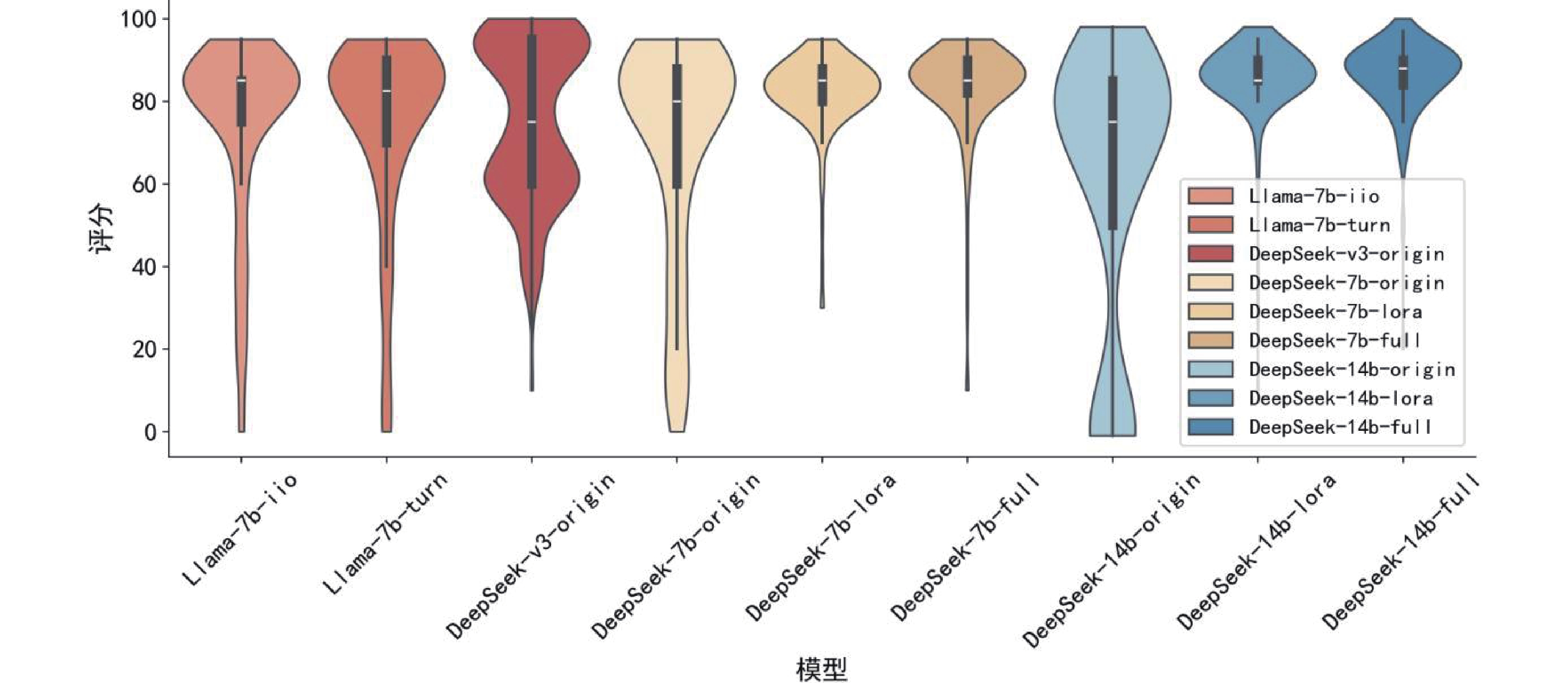
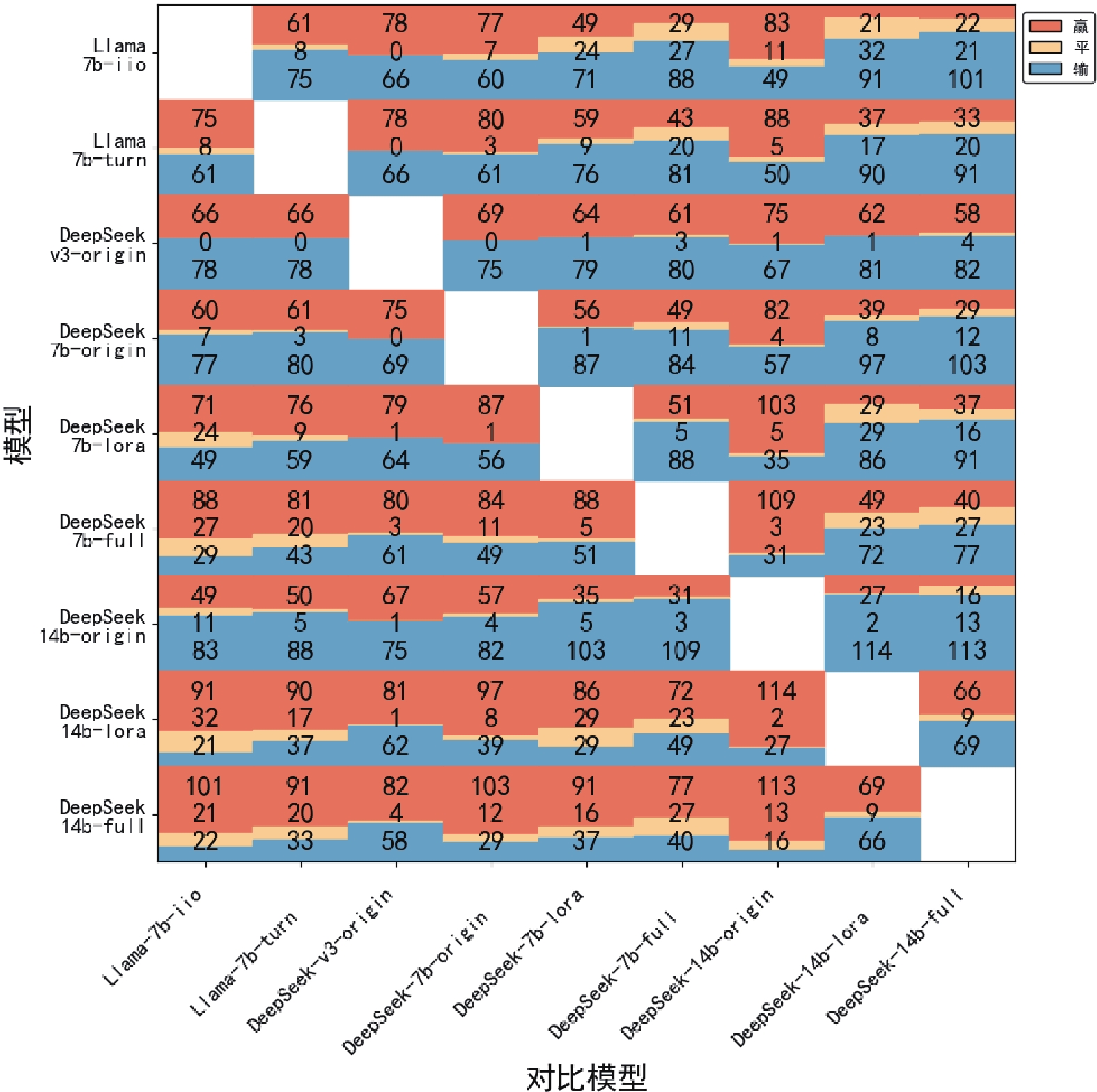
Figure/Table detail
LEAD-Cyber:a local fine-tuned vertical domain LLMs for cybersecurity with open-source LLMs and full-cycle training datasets
Journal of Cybersecurity,
DOI: 10.20172/j.issn.2097-3136.250116
| 种类 | 样本数 | Tokens | 平均Token |
| 网络安全新闻 | |||
| 网络安全数据集 | 471.9 | ||
| 网络安全网站 | 856.3 | ||
| 网络安全维基百科 | 124.8 | ||
| MITRE数据库 | 702.8 |
Table 1 Pre-training Dataset statistics
Other figure/table from this article